Cryptowall Removal Guide
Cryptowall is a Trojan virus which acts as a ransomware on the affected Windows operating systems. The dangerous threat attacks silently and in most cases it is spread using corrupted spam email attachments. Unfortunately, not all computer users have their operating systems guarded and not all of them are careful when browsing the web, downloading software or opening spam emails. This is a serious security backdoor which cyber criminals could use to initiate various virtual scams. Therefore, we advise that you start acting more carefully. Note that the Trojan can also enter the system using fictitious installers. If you are offered to update your media players, Java or Flash software, you should ignore these offers and visit official websites representing authentic updates. If you are not careful, soon enough you may need to delete Cryptowall or remove other dangerous threats from your own PC.
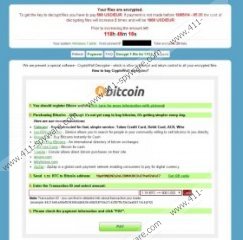
Cryptowall comes from the same faction of ransomware as Cryptolocker, Cryptorbit, Cryptodefence, and various others. These infections can enter the Windows system without permission and encrypt files existing on the computer. As our malware researchers have discovered, the infection can affect .doc, .jpg, .pdf, and various other file formats. Within the folders of the encrypted files the infection also places Decrypt_Instruction.txt, Decrypt_Instruction.html, Decrypt_Instruction.url files. If you click the latter one, a web page representing Cryptowall notification will be launched. This notification is not fictitious and ignoring it is not something you should do. Even though most ransomware infections present false information to lure out your money, the only fictitious part of this alert is the provided decryption solution. Even though the notification informs you that you need to pay a certain sum to have the files decrypted, there is one more thing you can try. Here is an excerpt from the alert.
Your files are encrypted.
To get the key to decrypt files you have to pay 500 USD/EUR. If payment is not made before [date] the cost of decrypting files will increase 2 times and will be 1000 USD/EUR
The malicious, devious ransomware can connect to the Internet without permission to send the key which is meant to eliminate the RSA 2048 file encryption. Fortunately, this key is likely to be found on your very own personal computer. Even though the location of the file can change, you can start looking for it in the %TEMP% or %Program Data% folders. If you can find unfamiliar .cert, .crt, .pfx, files, it is likely that one of them will help you decrypt the encrypted files. If you have found the key, we recommend that you install an automatic malware remover which will remove Cryptowall. If you skip this step, it is possible that right after you decrypt the files, the ransomware will encrypt them again. If you cannot find the decryption key, you can also try to use the instructions presented below.
How to decrypt files?
- Open the Start menu and select Control Panel.
- Select User Accounts and Family Safety and move to User Accounts.
- Now click Manage your file encryption certificates in the menu on the left. Click Next.
- Mark Use this certificate and select the detected certificate.
- Now click Select certificate and again click the Next button.
- Select Backup the certificate and key later and click Next.
- Finally click All logical drives and select the Next button.
The infection can evolve leaving these instructions helpless. If you are having trouble decrypting the files and removing the infection - contact us via the comment section below. We will try to help you restore your files.
Cryptowall Screenshots:



Comments
Where do I find "Manage your file encryption certificates" in Windows XP. User Accounts has nothing like that and the "User Account and Family Safety" doesn't exist in Control Panel