File Recovery Removal Guide
File Recovery is the latest computer infection that does not inform the user about its installation and invades the system unnoticed. This infection is similar to such malicious applications as Data Recovery. The rogue infects the system after installation of malicious applications or a Trojan. Hence, be aware of the danger of downloading and using suspicious programs that may torture your PC’s system after the installation.
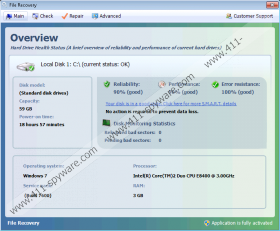
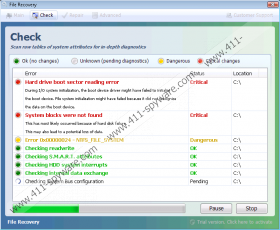
When File Recovery is on your computer, you may notice that something strange is going on your machine. You might not find some files or folders, which are not deleted but hidden by the malware. Not surprisingly, File Recovery operates like the vast majority of malware having an interface – the rogue wants to obtain your money and attempts to do so by presenting misleading information. You will find that your system is supposedly scanned and that some errors related to the registry, hard disk, RAM and GPU are presented. File Recovery presents such errors that, if actually present, would not allow you to use the computer at all. As most of the targeted computer users do not know how to solve different computer errors, it is likely that they will place their trust in File Recovery and, instead of deleting it from the system, will purchase its simulated “full” version that fix those supposed errors. This usually may happen after the presentation of such bogus errors:
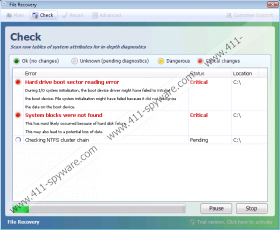
Hard Drive Boot Sector Reading Error
During I/O system initialization, the boot device driver might have failed to initialize the boot device. File system initialization might have failed because it did not recognize the data on boot device.System blocks were not found
This is most likely occurred because of hard disk failure.
This may also lead to a potential loss of data.
As the malware presents tons of different errors, it may also slow down your system’s performance to make you think that it occurs because of those errors. Please, pay no attention to the errors presented but remove File Recovery from your system as soon as you can. There is no need to trust a bogus application, because you can use a legitimate one that will surely take care of your system.
It might not be easy to remove File Recovery if it does not allow you to run certain applications. Usually, after fake-registration of the rogue, all simulated impairments disappear, and the user can terminate the infection. To simplify the removal of the malware, try registering it with the key provided with an imaginary email address:
08869246386344953972969146034087
Download a legitimate spyware removal tool to remove this bogus application. It is highly advisable to remove any rogue with appropriate software, because all the elements of the infection are detected and removed from the system. If you are an experienced computer user and know how to delete File Recovery, you can try to eliminate it from the system manually, but note that you should not left any element of the infection to prevent further download of malware to your machine.
File Recovery Screenshots: