TeslaCrypt Ransomware Removal Guide
The malicious TeslaCrypt Ransomware is not a secretive threat. Even though the infection can enter your operating system without your permission, it does not hide its intentions. Right after execution, the infection displays a notification that informs you that your personal files were encrypted and that you need to follow certain demands to regain full control over these files. According to our researchers, the infection can encrypt .jpeg, .pptx, .docx, .DayZProfile, .menu, .layout, .blob, and other game files. You should not rush to delete TeslaCrypt Ransomware, if the files encrypted are important to you, and you do not have any other way to access them. It is best to start worrying about the removal of the ransomware after making the decision about your personal files.
TeslaCrypt Ransomware is also known as CryptoLocker-v3. This is the name that was given to the threat by its developers, but our researchers indicate that it not a clone of the infamous Cryptolocker. Of course, the threat is similar to the infection, as well as ZeroLocker, Coin Locker, and other infamous ransomware infections whose removal we have reviewed in the past. These threats are mostly distributed using drive-by download attacks (e.g., corrupted spam email attachments), and none of them need permission to enter your operating system. As soon as TeslaCrypt Ransomware is executed, the threat terminates the processes taskmgr, msconfig, and regedit. These processes are needed for the removal of TeslaCrypt Ransomware, which is why having them terminated is very irritating. Luckily, this activity is temporary and, in most cases, computer users can regain access to Registry Editor, Task Manager, and other utilities soon after the execution of the ransomware. Of course, it is unlikely that you will rush to remove TeslaCrypt Ransomware after facing these intimidating statements.
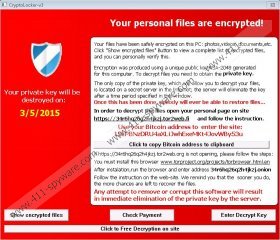
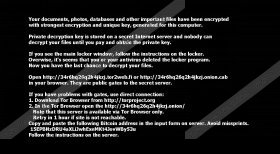
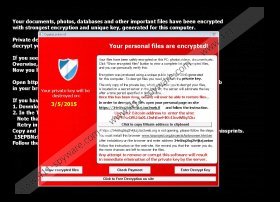
Your documents, photos, databases and other important files have been encrypted with strongest encryption and unique key, generated for this computer.
Private decryption key is stored on a secret Internet server and nobody can decrypt your files until you pay and obtain the private key.
Any attempt to remove or corrupt this software will result in immediate elimination of the private key by the server.
Luckily, the devious TeslaCrypt Ransomware does not encrypt executable files, which means that you should be able to launch your browsers and research the infection. The last thing you should do is rush into following the demands of the ransomware which include downloading a Tor Browser and using it to make a BitCoin payment for the so-called private key. Unfortunately, it is impossible to predict if the private key will work the way it is supposed to or if your files will remain encrypted. Do you have copies of your personal files that you do not want to have removed? If you do, we suggest forgetting about the encrypted files and just removing TeslaCrypt Ransomware.
As mentioned previously, TeslaCrypt Ransomware does not completely paralyze your operating system, which means that the removal of TeslaCrypt Ransomware should not cause much trouble. In fact, our researchers believe that all you need to do is install a reliable automatic malware removal tool and let it delete the infections installed on your operating system. After the removal is complete, we recommend taking the time to back-up your personal files. It is also important that you keep authentic security software updated at all times to ensure that threats like TeslaCrypt Ransomware could not attack again.
How to delete TeslaCrypt Ransomware
- Open the browser of your preference.
- Type http://www.411-spyware.com/download-sph into the address bar and tap Enter.
- Follow the on-screen instructions to install a reliable malware remover SpyHunter.
- Scan your operating system and remove TeslaCrypt Ransomware.
TeslaCrypt Ransomware Screenshots: