Windows AntiBreach Tool Removal Guide
Windows AntiBreach Tool is a malicious infection which may be dropped onto your personal computer by devious Trojans, with the help of misguiding social engineering scams, or via clandestine online scanners. Once the malicious files composing the infection are infiltrated, you may notice that your operating system is running slower than usual. Additionally, you may discover inability to run executable files or connect to the web. Unfortunately, many computer users link these symptoms to the fictitious PC threats listed by a bogus computer scanner. Even though the malicious computer threat is represented as an authentic, reliable malware detection and removal tool, there is no doubt that it is just another rogue you need to delete. How can you delete Windows AntiBreach Tool from the PC?
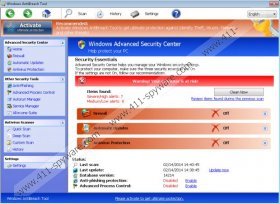
Do you know anything about the origins of Windows AntiBreach Tool? This clandestine threat is a true masterpiece of cyber criminals who are also known to have created Windows Efficiency Master, Windows Antivirus Master, and similar fake anti-spyware programs. All of these clandestine infections use the same misleading interface which is presented with a Windows shield logo, Firewall controls and other familiar attributes. Needless to say, the devious rogue has been created in a way to trick Windows users that it is a legitimate and beneficial malware remover. While the interface of the rogue is the first sign that this is not a legitimate malware remover, computer users may discover that the displayed pop-ups are fictitious as well.
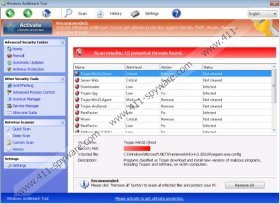
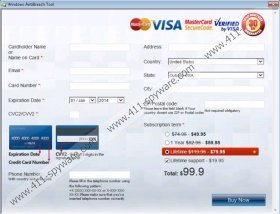
Those who click the buttons indicating alleged malware removal of virtual security activation will find themselves in the Windows AntiBreach Tool purchase page. Even though you may be pushed into believing that you need to purchase the full feature version of the rogue in order to have all existing threats deleted from the system, we can assure you that you will not benefit from this. If you spend your money on the allegedly beneficial tool, the fictitious threats will be ‘removed’ from the scanner to trick you into thinking that it worked. Unfortunately, this is just scam to take your attention away from the existing rogue which sooner or later could expose security vulnerabilities and help the infiltration of other malicious threats. For these reasons you should remove Windows AntiBreach Tool instantaneously.
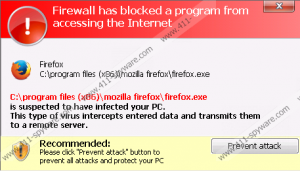
The malicious rogue is known for blocking system’s executables, and this is meant to stop you from installing automatic malware detection and removal software which would delete Windows AntiBreach Tool. You can disable these symptoms by registering as a valid rogue’s user. Luckily, you do not have to pay the requested payments! All you have to do is locate the area dedicated to existing rogue’s users and apply one of the registration codes listed below.
Registration codes:
0W000-000B0-00T00-E0001
0W000-000B0-00T00-E0002
0W000-000B0-00T00-E0003
0W000-000B0-00T00-E0011
0W000-000B0-00T00-E0022
0W000-000B0-00T00-E0023
0W000-000B0-00T00-E0031
0W000-000B0-00T00-E0032
0W000-000B0-00T00-E0033
As soon as the codes are applied you need to remove Windows AntiBreach Tool from the computer. Even if you cannot see any harm related to the threat yet, the infection is running on the PC, and it is only a matter of time before it could take over your personal computer again. What should you do if the registration codes do not work? In this case you can follow the instructions below. Even though this removal guide looks intimidating, we can guarantee success if you follow it step by step.
Delete Windows AntiBreach Tool from the PC
- Begin by restarting your personal computer.
- Start tapping F8 as soon as BIOS informing about hardware loads up.
- In the appeared menu navigate to Safe Mode with Command Prompt (use arrow keys).
- Tap Enter to confirm your selection and wait for the PC to boot up.
- In the Command Prompt enter cd.. after to C:\Windows\system32\ and tap Enter.
- As the C:\Windows line shows up enter the command \explorer.exe and tap Enter.
- Open the Start menu and launch RUN (Windows XP) or access the Search box.
- Enter %appdata% and the Application Data folder will show up.
- Locate svc-[random file name].exe, right-click the file and select Delete.
- Restart the computer again but this time in Normal Mode.
- Open the Start menu again and enter regedit into the RUN/Search boxes.
- In the Windows Registry move to HKEY_CURRECT_USER\Software\Microsoft\Windows NT\Current Version\Winlogon and right-click Shell.
- Select Modify and enter %WinDir%\Explorer.exe as the Value. Click OK.
- Launch the browser and visit http://www.411-spyware.com/download-sph .
- Download and install an automatic malware remover which will delete the existing malware.
Windows AntiBreach Tool Screenshots: