Windows Defence Unit Removal Guide
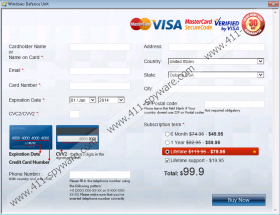
Some Windows operating system owners believe they can trust Windows Defence Unit; however, this is a mistake. Even though the tool looks like a regular malware removal application which is meant to keep your personal computer guarded against all virtual threats, in reality this is a rogue anti-spyware which presents fictitious services. Do you want to pay money for a tool which cannot detect or delete malware? Of course you do not, which is why you should delete Windows Defence Unit the moment you find it running on the computer. Overall, you should have no doubts that the main objective behind the rogue is to lure out your money, and so you should not postpone its removal for another minute.
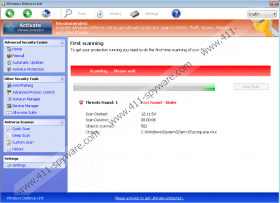
Even though Windows Defence Unit could be installed onto your personal computer secretly, it could be offered via fictitious online scanners as well. These scanners may be presented as banner warnings or could be opened in new windows. If you trust that malicious programs have corrupted your PC, you might install the offered malware remover; however, instead you should utilize a reliable and legitimate tool to make sure that real infections have corrupted your operating system. Unfortunately, many fall for the scam and end up installing Windows Defence Unit or any of its clones from the Rogue.VirusDoctor (or FakeVimes) family – Windows Protection Tool, Windows Protection Booster, etc. Once installed, the fake AV performs a fictitious computer scan and urges you to remove allegedly existing infections. This is when you are informed that you are using a trial version:
Recommended: Activate Antivirus to get full protection against malicious, virus, spyware and unwanted software
Trial version
Please purchase the full version of the software to ensure the ultimate protection
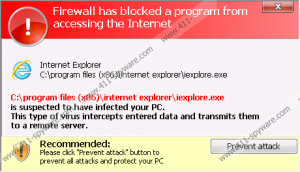
This is not a recommendation that you should follow. Of course, you may think that Windows Defence Unit is the only malware remover which could help you delete dangerous computer infections because they might have blocked access to the web browsers, Task Manager and other utilities. In reality, the executable files are blocked by the rogue itself in order to make it more difficult for you to remove Windows Defence Unit yourself. This is extremely deceitful and malicious, which is why you should not give in and help schemers generate profit. What we suggest is applying a special activation key to trick the fake AV into treating you as a legitimate user of the rogue anti-spyware. If this trick is successful, all existing symptoms should be disabled allowing you to delete the threat from the operating system freely.
Activation keys:
0W000-000B0-00T00-E0022
0W000-000B0-00T00-E0021
One of the activation keys should activate the full version of the clandestine rogue anti-spyware. Even though you might be tempted to postpone Windows Defence Unit removal after your PC returns to regular running, we advise that you delete the rogue right away. If you are not experienced with manual malware removal, we strongly recommend installing authentic Windows security software to ensure that all threats are removed and that your operating system is protected in the future. What should you do if the activation keys do not work? We have prepared the steps you can follow to install automatic malware removal software.
Delete Windows Defence Unit
- Restart the computer.
- Wait for BIOS screen to disappear.
- Instantaneously start tapping F8.
- As the advanced boot options menu shows up – use arrow keys to select Safe Mode with Command Prompt.
- Tap Enter on the keyboard to confirm your selection.
- In the command prompt window place the cursor after C:\Windows\system32\ and enter cd.. to access the C:\Windows line.
- Now type explorer.exe and tap Enter on the keyboard.
- Open the Start menu (click the icon located on the left of the Task Bar).
- Click RUN/Search and enter %appdata% to access the Application Data.
- Now right-click svc-[random file name].exe and select Delete.
- Restart the PC again but this time in Normal Mode.
- Click the Start icon on the Task Bar again to open the menu.
- Click RUN/Search and enter regedit to access the Registry Editor.
- Move to HKEY_CURRECT_USER\Software\Microsoft\Windows NT\Current Version\Winlogon .
- Locate the Shell and right-click it.
- Select Modify and enter %WinDir%\Explorer.exe into the Value box. Click OK.
- Now launch a browser and go to http://www.411-spyware.com/download-sph .
- Follow the provided instructions to download and install an automatic malware removal tool which will help you delete all existing computer infections.
Windows Defence Unit Screenshots: