Windows Secure Web Patch Removal Guide
Windows Secure Web Patch can easily pull the wool over your eyes if you rely on this fraudulent application which is a clone of Windows Instant Scanner, Windows Privacy Counsel and other simulated security tools. As a clone and a fraudulent application, Windows Secure Web Patch is attributed to Rogue.VirusDoctor family which consists of rogues sharing identical characteristics. This rogue is a well-organized scheme of cyber criminals to get money paid by gullible Windows users. Windows Secure Web Patch declares that such infections as Trojans, viruses, key loggers, worms, etc are removed once it is activated or registered.
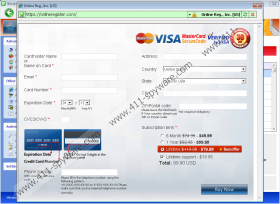
The registration or purchase of the rogue is not advisable due to the fact that Windows Secure Web Patch is not a real security tool. If the rogue is purchased, it means that money and personal financial information such as credit card number, CVV/CVV2, login passwords are lost as well as money paid for the application. The activation of Windows Secure Web Patch only helps to remove it manually, but this will be discussed later. However, do not make any payments but remove the rogue.
When Windows Secure Web Patch invades the system, it takes full control of the system. The system might start running slower due to the changes made in the system. For example, Internet connection is no longer in your control, because the rogue disables the connection to prevent its removal from the system by using a removal tool downloaded from the Internet. The malware also modifies Registry Editor and hides it from users. In Registry Editor, many new registry entries are created to block executable files from running. Instead, the infection introduces its own processes. Moreover, to hide its processes, Windows Secure Web disables Task Manager.
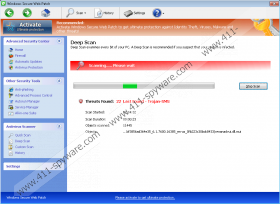
As Windows Secure Web Patch pretends to be a computer security tool, it fakes functions of real antivirus programs. After a simulated scan, the rogue displays a list of infections. You might find such infections as Trojan-Downloader.Win32.Agent, Rootkit.Win32.KernelBot, Backdoor.Win32Rbot and others. Pay no attention to these infections, because they are not existent in the system. Soon after the installation, Windows Secure Web Patch spreads many files which are named as Trojans, worms or malware, which you should not be afraid of, because they are not harmful to the system. The only harmful infection is the rogue itself, because if you do what cyber criminals expect you to do, you will suffer negative consequences such as money and sensitive data loss.
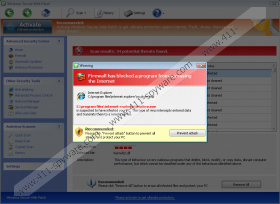
Windows Secure Web Patch employs various notifications to scare you into believing that the system is infected. The notifications might seem to be convincing and professionally looking; moreover, they are difficult to get rid of, because they do not stop popping up on the screen. For example, you might find these warnings:
Error
Potential malware detected.
It is recommended to activate protection and perform a thorough system scan to remove the malware.Error
Attempt to run a potentially dangerous script detected. Full system scan is highly recommended.Error
Software without a digital signature detected. Your system files are at risk. We strongly advise you to activate your protection.
If you want to bring an end to the deception, a removal of the infection is a must. There are two options for the removal of Windows Secure Web. If you want to delete the rogue own your own, activate the malware with this activation key 0W000-000B0-00T00-E0020 so that you can access Registry Editor from which you have to delete the malign registry entries. Moreover, you have to terminate the processes of the rogue and delete certain files. If you the procedure is too tricky, delete Windows Secure Web Patch automatically. A malware removal tool is necessary in this case. Note that you have to be sure that you use a legitimate tool to terminate the infection; otherwise, a fake antispyware might cause more damage to the system. If the removal tool is legitimate, the rogue will be deleted, and the system will be protected.
Windows Secure Web Patch Screenshots: