Philadelphia Ransomware Removal Guide
Perhaps people have urged you countless of times to delete spam email messages the moment you find them in your inbox, but you probably have never thought that one of them could infect you with Philadelphia Ransomware. This ransomware infection travels via phishing emails, and so it cannot really enter your computer at will. It will only get installed on your system if you open the installer file yourself. Likewise, you will also need to remove Philadelphia Ransomware, too. The removal process is not that complicated, but it may not be enough to delete all the malicious files. Thus, you should also get yourself a legitimate antispyware application.
This program comes from a group of similar applications. Usually, we have the same developers creating several clones of the same program and spreading them around. With Philadelphia Ransomware, we have an original program that functions as a pattern for further customization. During our tests, we have found that Philadelphia Ransomware is based on the Stampado ransomware application. That is not to say the developers of Stampado have released a new infection. It is actually a lot more likely that the owners of this new infection have modified the older one according to their likes and preferences.
That is to say, someone BOUGHT Philadelphia Ransomware from its developers, customized it, and sent it out in the open to “work.” In other words, this program is the so-called Ransomware-as-a-Service that can be bought on the darknet. Later on, it spreads via phishing email messages, and when users open attachments from such emails, the infections slithers into their computers. Aside from that, the program can also be spread via fixed, removable and network drives, and drive root folders. So, if an infected flash drive is plugged into your computer, you may get infected with this program, too.
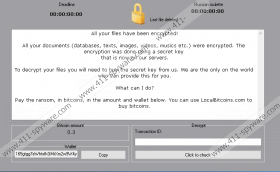
When the program finally enters your computer, it employs the so-called “Russian Roulette” tactics. If the program is enabled, it turns on a counter, and when it goes down to zero, a certain predetermined number of files will be deleted from your computer. For the encryption, this program will use a custom encryption algorithm (which only proves that the program itself has been customized as well). It will encrypt a big number of your documents, but the program does not touch your browsers and Windows system files because it still needs your computer to function. Otherwise, you would have no way to transfer the ransom fee.
Philadelphia Ransomware expects you to pay 0.3BTC (around $182USD) for the decryption key. Of course, that is out of the question because paying would mean giving your money away and allowing these criminals to win. Albeit there is no public decryption tool for this ransomware variant as of now, the files affected by Stampado ransomware can be decrypted, so there is hope that sooner rather than later they will also release a decryption tool for Philadelphia Ransomware.
If you do not want to wait, you can delete Philadelphia Ransomware right now, and then restore your files from a backup. This backup can be en external hard drive or a cloud storage drive. Or perhaps you even keep the most important files on your other computer or some mobile device. The most important thing is to terminate the infection before you transfer back your files. Should you have any further questions, please do not hesitate to leave us a comment below.
How to Delete Philadelphia Ransomware
- Press Win+R and type %AppData%.
- Click OK and go to Roaming.
- Locate and delete the lsas.exe file.
- Press Win+R again and the Run prompt will open.
- Type regedit into the Open box. Click OK.
- Navigate to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run.
- Delete the Windows Update key.
- Scan your system with SpyHunter.
Philadelphia Ransomware Screenshots: