CryLocker Ransomware Removal Guide
CryLocker Ransomware is a new dangerous threat that surfaced at the beginning of September, 2016. This infection seems to be very similar to Cry Ransomware that has also hit the web only recently. As a matter of fact, it looks like this new program was also created by the same RAAS (Ransomware As A Service) that is most likely promoted on the Dark Web. Unfortunately, there is little chance that you will see or use the files which get encrypted with this ransomware again Well, unless you are a cautious computer user and you keep a backup copy of your most important files on a separate, external drive. Obviously, these criminals want your money in return for the private key and the decryption tool. But you should keep in mind who you are dealing with here. It is quite possible that these crooks will simply take your money and you will never hear from them again. We believe that if you want to restore the virtual security of your computer, you need to remove CryLocker Ransomware immediately, without any hesitation. Let us help you with that, but, before revealing the solution, we would like to share our findings with you regarding this major attack.
This ransomware program started to spread via Exploit Kits. First time it emerged on the web it used the so-called Rig Exploit Kit to infect unsuspecting computer users. But a few days later it was found spreading through other kits as well. You can let such serious threats as this one onto your system through these kits when your browsers and drivers, such as Adobe Flash Player and Java, are not updated regularly. These Exploit Kits are used to set up fake websites with malicious content, including flash banners and Javascript, that can drop this ransomware or any other onto your computer once you load these pages. You may not know but it is enough to click on a corrupt link or third-party ad for you to end up on such a malicious website. This can happen when your computer is infected with adware programs or browser hijackers. These innocent-looking infections can expose you to unreliable ads and links, which can redirect you to websites particularly set up to infect you with dangerous malware programs. If this is how you may have let this beast on board, you should make sure you update all your programs and drivers right after you delete CryLocker Ransomware.
Another possible way for this malware infection to enter your PC is via spam e-mails using Trojans. This means that you may find a spam mail in your inbox that has an attachment. This attached file is indeed a Trojan that poses as a “must-see” image or text file. The made-up sender address and the subject can convince you that this is an important mail that you must open right away as well as save the attachment and view it. However, once you click to open the downloaded file, you will not simply view a fake unpaid invoice claim or a complaint about wrong credit card details, but you will also initiate the download and activation of CryLocker Ransomware silently in the background. This is why we ask you to be more alert when browsing your inbox. Because even if you remove CryLocker Ransomware after you notice it, your files will be encrypted and you will not be able to recover them unless you pay the ransom fee and get lucky to get anything in return.
After you start up this vicious program, it drops its malicious files either in the "%TEMP%" folder or in the "%ALLUSERSPROFILE%" folder with a random 8-character name. This ransomware is very destructive as it targets hundreds of file extensions, which means that you may lose most of your files in this ugly attack. The authors claim that this threat uses the 4096-bit RSA algorithm to encrypt your files; however, we cannot confirm this yet. The affected files get a ".cry" extension, which clearly shows what kind of infection has taken them hostage. Interestingly enough, this ransomware program does more than “just” encrypting your files.
In the background it also collects your WiFi Access Point information, attempts to get your geo-location, and checks the system's language identifier. If it detects the following languages, the threat cancels its action: Belorussian, Kazakh, Russian, Sakha, Ukrainian, and Uzbek. Apart from all these activities, it also deletes the Shadow Volume Copies of your files so that they cannot be restored through your Windows operating system. When it finishes all its operations, a ransom note image blocks your screen. In fact, this is the only file or document that contains the name “CryLocker.”
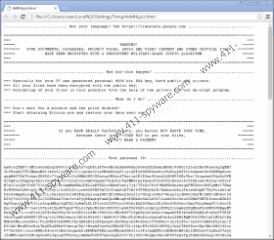
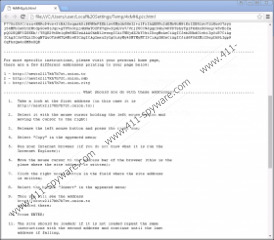
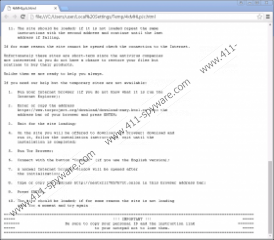
From this note you learn that your files have been encrypted and can only be restored if you follow the instructions in the given files ("!Recovery_[6 characters].txt" or "!Recovery_[6 characters].html"), which can be found on your desktop. These are quite lengthy documents explaining in detail what and how you should do to transfer the ransom fee in order to get the private key and tool necessary for you to be able to recover your files. You have to access a personalized website that may look a bit scary for inexperienced users since it looks like you have been fined by some legal authority. These crooks seem quite “hungry” as the ransom fee this time is $625 that has to be paid and transferred in Bitcoins. We do not recommend that you do so; however, this is absolutely your decision to make. We suggest that you delete CryLocker Ransomware right away.
If you have set your mind and are ready to act, here we are with the solution. Please use our instructions below to make sure that all the components of this threat get where they belong – to your Recycle Bin. It is possible that you do not feel up to this task or any manual detection and cleaning; therefore, we advise you to use a reliable anti-malware program, such as SpyHunter, that can automatically detect and eliminate any known malware threats as well as protect your system from further attacks. Once you install such security software, you should keep it all the time active and up-to-date as well for best results.
How to remove CryLocker Ransomware from Windows
- Press Win+E.
- Delete the malicious file you saved from the spam e-mail.
- Check “%ALLUSERSPROFILE%” and “%TEMP%” directories for any suspicious files with random name and delete them. (If you want to make sure it is a malicious file, you should use a reliable online file scanner to determine this.)
- Bin the ransom notes from the “%TEMP%” directory and your desktop.
- Delete the shortcut that points to the ransom note inside “%TEMP%” directory:
For Windows XP: “%ALLUSERSPROFILE%\Start Menu\Programs\Startup”
For newer Windows users: “%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup” - Empty your Recycle Bin.
- Restart your computer.
CryLocker Ransomware Screenshots: