PooleZoor Ransomware Removal Guide
PooleZoor Ransomware is a real threat. We cannot underestimate it. At its current state, it only encrypts files found on the Desktop, and the ransom note presented along with the encrypted files does not make a lot of sense. That being said, no one knows when the threat could be upgraded. Our malware researchers are closely monitoring the arrival of new threats or new variants of well-known malware, and so if something new is discovered, we will inform you right away. In the meantime, let’s discuss the current version of the ransomware, and why removing it is so important. While that might be self-explanatory – considering that the infection does not hide its true face – it might be harder to understand the state of the encrypted files. Note that they cannot be restored by deleting PooleZoor Ransomware. Are you curious to learn more? If you are, continue reading. And do not forget to leave a comment below if you have any questions or observations.
Spam emails. This is what you need to be extra careful about if you do not want to let malware in. All kinds of malicious infections can be distributed via misleading links and files attached to emails, but our researchers warn that most ransomware is spread using this security backdoor. If you are tricked into executing the infection, it might be hard for you to understand that malware exists at all. On the other hand, if you have downloaded or opened a file that does not represent the content you thought it would, or that does not open at all, a safe bet would be to remove this file right away. Hopefully, you can remove PooleZoor Ransomware before it is fully executed and before it obtains an encryption key. If you do not act fast, the infection can start encrypting your personal files without your notice. It is not yet known which encryption method is used, but it is known that the “.poolezoor” extension is appended to the corrupted files’ names. It is also known that the threat is programmed to encrypt files with ".apk", ".accdb", ".xlsx", ".pptx", ".ppsx", ".rar", ".zip", ".pdf", ".txt", ".doc", ".docx", ".xls", ".ppt", ".pptx", ".odt", ".jpg", ".png", ".csv", ".sql", ".mdb", ".sln", ".php", ".asp",".aspx", ".html", ".xml", and ".psd" extensions.
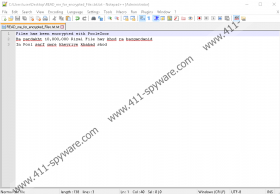
Just like PTP Ransomware, AndreaGalli Ransomware, and most other infections created using the Hidden-Tear open source code, PooleZoor Ransomware is not fully functional. As discussed already, it does not encrypt lots of files, and it does that on the Desktop only, which is strange. It was also found that the ransom note represented by PooleZoor Ransomware does not make sense. Victims of this malware can find the note in the READ_me_for_encrypted_Files.txt file on the Desktop. What does the ransom note say? In English, it says that files were encrypted. In Persian, it says that 10 million Iranian Rials must be transferred if the victim wants to decrypt corrupted files. This is pretty much what you can expect from any ransomware. The unusual thing is that there are no instructions on how to make the payment, which is why it is believed that the ransomware is either unfinished and is waiting an upgrade, or that it simply does not work. In any case, it requires removal.
If files were encrypted by PooleZoor Ransomware, you could not recover them, and even if you were able to pay the ransom, you are unlikely to get a decryptor. Ransomware is built by cyber criminals, and they do not care whether or not you get your files back. This stands true for most if not all ransomware threats. So, what are you supposed to do? Take this as a lesson. You can protect your files in the future by backing them up, but do not use your system’s backup because some infections can destroy it. Instead, use cloud storage or external drives. If you already have backups, and you can recover your files, we suggest removing PooleZoor Ransomware first because you do not want to connect to any kind of storage while malware is still active. How can you delete this malware? You can do it manually if you know where the .exe file is and you know how to use a malware scanner, or you can employ anti-malware software. Choose the latter option if you also need full-time protection; and you definitely do need it.
How to delete PooleZoor Ransomware
- Find the {unknown name}.exe file that is the launcher (examples: hidden-tear.exe, hello.exe, payment.exe, Peyment.exe).
- Right-click the file and then choose Delete.
- Go to the Desktop and Delete the ransom note file called READ_me_for_encrypted_Files.txt.
- Install a trustworthy malware scanner and employ it for a full system scan.
PooleZoor Ransomware Screenshots:
PooleZoor Ransomware technical info for manual removal:
Files Modified/Created on the system:
| # | File Name | File Size (Bytes) | File Hash |
|---|---|---|---|
| 1 | a5e5e6712d2dfe41e7e0e725460f2579cfc4e8a7a835e4d8e528f1999959c32f.exe | 211456 bytes | MD5: f35a0b7d05bdd7de637c54023aaf4412 |
Memory Processes Created:
| # | Process Name | Process Filename | Main module size |
|---|---|---|---|
| 1 | a5e5e6712d2dfe41e7e0e725460f2579cfc4e8a7a835e4d8e528f1999959c32f.exe | a5e5e6712d2dfe41e7e0e725460f2579cfc4e8a7a835e4d8e528f1999959c32f.exe | 211456 bytes |

