CtrlAlt Ransomware Removal Guide
CtrlAlt Ransomware is a threat that enciphers user’s data and gives a second .altdelete@cock.li.district extension to each locked file. If your files are marked this way, we recommend reading this article carefully so you could learn all the essential details about this malicious application. Further, in the text, we will talk about how CtrlAlt Ransomware might enter the system and what happens if it does as well as what we recommend doing after the computer gets infected. A bit below the text readers will find our prepared deletion instructions that will tell how to get rid of this malicious program manually. The malware can be erased with a security tool of your choice too, so if you decide to remove this threat, so if the instructions seem to be too difficult do not hesitate to employ a reliable antimalware tool.
The malicious application is most likely spread the same way as other similar threats. Usually, our encountered ransomware programs travel with malicious email attachments, software installers, updates, pop-up advertisements, and other content received or downloaded from untrustworthy sources. Thus, for those who wish to keep away from CtrlAlt Ransomware and threats alike, we would advise not to open doubtful files before scanning them with a reliable security tool first. However, it is natural, it would be even safer not to download unreliable content in the first place. To be more precise, our specialists say users should avoid attachments from unknown senders, installers from torrent sites, and so on. Another thing we would advise for those who like being extra cautious is keeping a reliable antimalware tool installed and up to date as it can warn about various malicious applications.
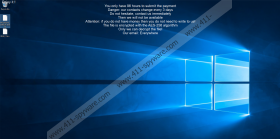
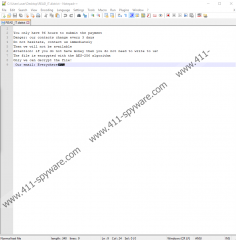
The moment the malware settles in it should start encrypting user’s data. According to tour specialists, CtrlAlt Ransomware does not encrypt files located on the following folders: Default, All Users, ContentIE5, Temporary Internet Files, Local Settings, AppData, Program Files (x86), Program Files, Windows, Microsoft, Program Data, Intel, Recycle.Bin, NVIDIA, System Volume Information. All other data should receive the malicious application’s extension (.altdelete@cock.li.district) and become unusable. Once the encryption process is over, CtrlAlt Ransomware’s victims should see a ransom note called READ_IT.district. Also, the same text found inside of the note should be on the user’s wallpaper as the infection replaces it after the encryption process. The message from the hackers asks to contact them via email, but only if the victim has money. It means the malware’s creators intend to offer decryption tools in exchange for a ransom. What you should know is there are no guarantees they will deliver the promised too, which is why dealing with these people could be hazardous.
As you realize, we do not recommend paying the ransom. We believe it is safest to restore whatever files you can from backup copies. For safety measures, any attempts to restore encrypted data should be made only after removing CtrlAlt Ransomware, which is what you ought to do if you do not want to pay a ransom and risk losing your savings for nothing. One of the ways to eliminate the malicious application is to complete the steps located below. The second option is to employ a reliable security tool and perform a full system scan.
Get rid of CtrlAlt Ransomware
- Click Ctrl+Alt+Delete.
- Select Task Manager.
- Locate a process related to the malware.
- Mark it and press End Task.
- Exit Task Manager.
- Open File Explorer (Win+E).
- Go to these locations separately:
%TEMP%
%USERPROFILE%\Downloads
%USERPROFILE%\Desktop - Search for a suspicious file that might be the malware’s installer; right-click it and select Delete.
- Locate the ransom notes (READ_IT.district), right-click these files separately and select Delete.
- Exit the Explorer.
- Empty Recycle bin.
- Reboot the device.
CtrlAlt Ransomware Screenshots:
CtrlAlt Ransomware technical info for manual removal:
Files Modified/Created on the system:
| # | File Name | File Size (Bytes) | File Hash |
|---|---|---|---|
| 1 | f5d893afc4ad2e98606b597df186657b57f3d1e3a5abe51f800de6086aab84e9.exe | 411136 bytes | MD5: 5a131b48f147586afa20b0a1a00a1533 |
Memory Processes Created:
| # | Process Name | Process Filename | Main module size |
|---|---|---|---|
| 1 | f5d893afc4ad2e98606b597df186657b57f3d1e3a5abe51f800de6086aab84e9.exe | f5d893afc4ad2e98606b597df186657b57f3d1e3a5abe51f800de6086aab84e9.exe | 411136 bytes |

