Wal Ransomware Removal Guide
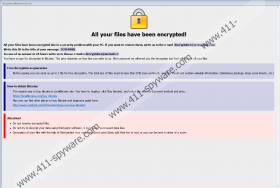
If Wal Ransomware enters your system, your photos, pictures, and other files that you might hold dear could become useless. This malicious application achieves this by encrypting its victims’ data with a secure encryption system. As a result, affected files need to be decrypted before they can be launched and, sadly, the necessary decryption tool could be impossible to come by. The hackers do offer the required decryptor via the message their threat displays after it encrypts targeted files, but it says a user has to pay a ransom for it. It would be no doubt a risky thing to do as you cannot be sure the malicious application’s developers will keep up with their promise. If you fear being scammed, you should look for other ways to get your data back, such as backup copies. To prevent further damage and clean your computer, we recommend removing Wal Ransomware with the deletion instructions located at the end of this article or your chosen security tool.
Our specialists report that Wal Ransomware is a new version of Crysis/Dharma Ransomware. It does not necessarily mean that the applications were created or are distributed by the same cybercriminals. Still, the hackers behind the new variant are likely to use the same distribution channels to spread it. As you see, Spam emails and malicious sites are probably the top two distribution channels used by ransomware developers. By sending their victims malicious and yet harmless-looking email attachments, the attackers can trick them into launching the threat themselves. Same could happen with fake installers, updates, and other files alike spread via unreliable file-sharing sites that offer pirated software, unknown freeware, and so on. Thus, if you do not want to infect your system accidentally, you should never open untrustworthy data without scanning it with a reliable antimalware tool first.
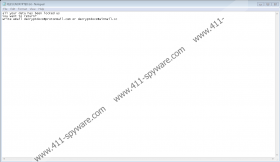
In case Wal Ransomware gets in it should create files it needs to settle in on a victim’s computer. If you want to learn what kind of files the malicious application needs and where it could be placed, you should scroll down and check our deletion instructions. After the threat installs itself, it should start encrypting photos, videos, and other files that could be precious to a victim. To make it clear which files are encrypted and can no longer be accessed, the threat ought to append a long extension that should be similar to this one: .id-4C9E095B.[decryptdocs@protonmail.com].wal. Naturally, the part with an ID number is supposed to be unique, while the hackers’ email and the .wal part should not change. Next, Wal Ransomware ought to open a ransom note in which users should see a message claiming all files were encrypted due to some problem with an infected computer’s security. Also, it ought to urge users to email the malware’s developers to learn how to pay a ransom and get the necessary decryption tool.
Even though the cybercriminals may claim they can guarantee you will get the promised decryption tool, you should know that it is not exactly true. The only thing the hackers can prove by encrypting one file free of charge is that the needed decryption tool is in their possession. In other words, no one can guarantee they will send it after receiving a payment. Provided, you do not want to take any chances, we advise removing Wal Ransomware.
If you think you can handle the task, you could complete the deletion instructions located below this article. On the other hand, if the process looks more challenging than expected, you may want to get a reliable antimalware tool that could erase Wal Ransomware for you.
Get rid of Wal Ransomware
- Tap Ctrl+Alt+Delete.
- Pick Task Manager.
- Select the Processes tab.
- Look for a process associated with the malware.
- Select the process and click End Task.
- Leave Task Manager.
- Tap Win+E.
- Go to these locations:
%TEMP%
%USERPROFILE%\Downloads
%USERPROFILE%\Desktop - Find the malicious file opened before the system got infected, right-click it and select Delete.
- Navigate to these paths separately:
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup
%WINDIR%\System32
%APPDATA% - Search for files named Info.hta, right-click them and select Delete.
- Navigate to these paths:
%WINDIR%\System32
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup - Identify malicious executable files, e.g., file.exe; right-click them and choose Delete.
- Close File Explorer.
- Tap Win+R.
- Type Regedit and click Enter.
- Go to: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Identify the malware’s created value name, e.g., file.exe, right-click this value name and press Delete.
- Locate this directory: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Find the malicious application’s created key, e.g., mshta.exe, right-click it and select Delete.
- Close Registry Editor.
- Empty Recycle Bin.
- Restart the computer.
Wal Ransomware Screenshots: