Dharma-Ninja Ransomware Removal Guide
Dharma-Ninja Ransomware could be on your system if your files are marked with a strange extension that ends with “.ninja.” This malicious application was designed to encrypt data that could be precious to its owner. By encrypting it, the hackers behind the malware take your files as hostages. Their ransom note should state that the only way to unlock them is to use unique decryption software. Also, the note should say that the size of a ransom depends on how fast a victim contacts the hackers. It is crucial to understand that cybercriminals may promise many things, but there are no guarantees they will hold on to their end of the deal. If you have no wish to take any chances, we advise you not to contact them. If you have backup copies, you could still get your files back by replacing encrypted data with copies. However, to be safe, we recommend removing Dharma-Ninja Ransomware first.
In the rest of our report, you can find more details about this malicious application. The first thing we ought to explain is how it might be distributed. Such information may help users avoid Dharma-Ninja Ransomware or similar threats. Most of such infections get in because victims get tricked into launching their installers. For example, hackers may send targeted users malicious email attachments that could look like documents, pictures, etc. The email itself could also look like a message from a reputable company or someone else you might trust.
Therefore, recognizing malicious emails might be a difficult task, although not an impossible one. The best way to protect yourself from such attacks is to be careful with emails that you receive unexpectedly or messages coming from unknown senders. Also, it is best to scan attachments that could come with questionable emails with a reliable security tool. Another thing we highly recommend is keeping away from unreliable file-sharing websites, as malicious launchers can be disguised as software installers, updates, etc.
After entering a system, Dharma-Ninja Ransomware should start encrypting your photos, various types of documents, archives, and other data you might consider valuable. As files get encrypted, they should receive a particular extension that is made from a unique ID number, the hacker’s email address, and the word “.ninja,” so we could say that it is partly unique to each victim. For instance, a file encrypted and marked with the malware’s extension may look like this: text.docx.id-3C9E098B.[ninja777@cock.li].ninja.
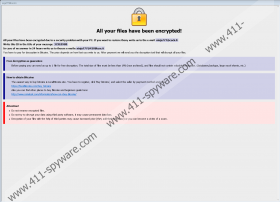
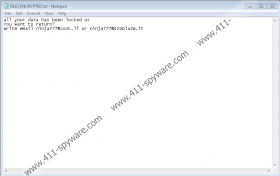
By the time the malicious application finishes encrypting files, it should create a couple of files called FILES ENCRYPTED.txt and Info.hta. Both of them might be scattered among directories mentioned in our removal instructions located below this report. The .txt file should contain a short message that claims users need to contact hackers behind Dharma-Ninja Ransomware via email. As for the other file, it ought to open a window with a longer message. In short, the text ought to explain what happened to your data and how you can purchase decryption tools if you pay a ransom.
Needless to say, it could be risky to deal with the Dharma-Ninja Ransomware’s developers. Consequently, we advise thinking carefully if you want to take any chances. If you do not, you should ignore the malware’s ransom note and erase it. One of the ways to eliminate Dharma-Ninja Ransomware is to use a reliable antimalware tool that would be capable of dealing with such a threat. We recommend making sure that your chosen tool is reputable and comes from a legit source if you do not want to end up downloading fake security software. The other way to remove this malicious application is to get rid of its files manually. If you need any guidance, you could follow the instructions located below. Note that if you cannot find the threat’s process, you could restart your device in Safe Mode instead of completing the first six steps.
Get rid of Dharma-Ninja Ransomware
- Tap Ctrl+Alt+Delete.
- Pick Task Manager.
- Select the Processes tab.
- Look for a process associated with the malware.
- Select the process and click End Task.
- Leave Task Manager.
- Tap Win+E.
- Go to these locations:
%TEMP%
%USERPROFILE%\Downloads
%USERPROFILE%\Desktop - Find the malicious file opened before the system got infected, right-click it, and select Delete.
- Navigate to these paths separately:
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup
%WINDIR%\System32
%APPDATA% - Search for files named Info.hta, right-click them and select Delete.
- Navigate to these paths:
%WINDIR%\System32
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup - Identify malicious executable files, e.g., file.exe; right-click them and choose Delete.
- Erase files called FILES ENCRYPTED.txt.
- Close File Explorer.
- Tap Win+R.
- Type Regedit and click Enter.
- Go to: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Identify the malware’s created value name, e.g., file.exe, right-click this value name, and press Delete.
- Locate this directory: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Find the malicious application’s created key, e.g., mshta.exe, right-click it, and select Delete.
- Close Registry Editor.
- Empty Recycle Bin.
- Restart the computer.
Dharma-Ninja Ransomware Screenshots: