Cyborg Ransomware Removal Guide
An extension called .petra placed on your files might mean you got tricked into launching a malicious application named Cyborg Ransomware. If it is true, files that have this extension should be encrypted with a strong encryption algorithm. It is essential to know that the only way to get your data back without putting up with hackers’ demands and risking your money is by replacing encrypted files with backup copies. To learn more about this, we encourage you to read the rest of our report. Also, if you are looking for instructions that would help you to remove Cyborg Ransomware manually, you could use the steps located at the end of this article. Of course, if you do not think you can erase this threat on your own even with the given instructions, we advise using a reliable antimalware tool instead.
Cyborg Ransomware is a sneaky threat as it might install itself by creating a hidden file in the %Homedrive% folder. The question is: how it gets in the first place? Our specialists say that the malware might be spread through unreliable P2P file-sharing networks, other untrustworthy websites, and Spam emails or other suspicious messages. Meaning, it could be received with files downloaded or obtained via the Internet.
Moreover, a victim could be tricked into believing that the malware’s launcher is a harmless file. For example, hackers could make the threat’s installer look like a text file. Also, websites or emails carrying/offering such installers might claim they are important documents or legit software installers, updates, etc. Therefore, to avoid malicious applications like Cyborg Ransomware, you have to pay close attention to data that you choose to download and launch, as well as make sure that it comes from reliable sources. If you are unsure about some file, you should not take any risks and scan it with a reliable antimalware tool first.
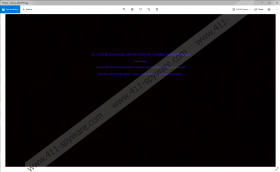
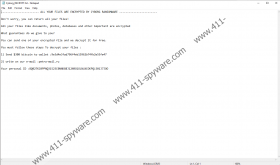
After creating the mentioned hidden file, Cyborg Ransomware should start encrypting files available in the following %USERPROFILE% subfolders: Desktop, Downloads, Documents, Pictures, Contacts, and Links. Data kept in other directories should not be encrypted, so if you do not have much of valuable data in the listed folders, the damage you receive after encountering this threat could be of a minimum amount. As soon as the malicious application encrypts targeted files, it should change your Desktop image with a black picture that ought to have a specific text in the middle of it. To be more precise, the picture’s text should ask you to view a document called Cyborg_DECRYPT.txt. We call it a ransom note since the message in it says a user has to pay 300 US dollars if he wishes to get his data back.
If risking your money for decryption tools you might never get does not sound like a good idea to you, we advise not to put up with any demands. As said at the beginning of our report, files can be replaced with backup copies if a user has them. Not to mention, the malware does not target a lot of locations, and the data it encrypts might not be worth paying a ransom. In any case, whatever is your decision, we advise not to leave Cyborg Ransomware unattended.
Users who wish to erase the malicious application manually should know that the task could be difficult. Still, if you think you can manage, we advise using the instructions located below. As for users who want to delete Cyborg Ransomware, but do not think they can do so manually, we recommend installing a reliable security tool that could remove this threat for them.
Restart the device in Safe Mode with Networking
Windows 8 and Windows 10
- Tap Win+I or navigate to the Start menu and click the Power button.
- Tap and hold Shift and click Restart.
- Select Troubleshoot and choose Advanced Options.
- Pick Startup Settings and press Restart.
- Click the F5 key and reboot the system.
Windows XP/Windows Vista/Windows 7
- Open Start, press Shutdown options and tap Restart.
- Press and hold the F8 key when your computer is restarting.
- Wait till you see the Advanced Boot Options window.
- Choose Safe Mode with Networking.
- Press Enter and log on to your computer.
Display hidden files and folders
Windows 8 and 10
- Open th0 File Explorer, click the View tab, and select Options.
- Choose change folder and search options.
- Press on the View tab, select Show hidden files, folders and drives, and click OK.
Windows 7 and Vista
- Go to Start, launch Control Panel, then select Appearance and Personalization.
- Open Folder Options, click the View tab, and mark Show hidden files, folders and drives.
- Select OK.
Windows XP
- Navigate to Start, launch Control Panel, then select Appearance and Themes.
- Click Folder options, choose the View tab, and select Show hidden files and folders.
- Click OK.
Get rid of Cyborg Ransomware
- Press Win+E.
- Go to these locations:
%TEMP%
%USERPROFILE%\Downloads
%USERPROFILE%\Desktop - Locate a recently downloaded suspicious file that could be the malware’s launcher.
- Right-click the malicious file and select Delete.
- Find this folder: %Homedrive%
- Locate the malware’s copy that might be called bot.exe, right-click it and select Delete.
- Find the malware’s ransom note (Cyborg_DECRYPT.txt), right-click it and select Delete.
- Close File Explorer.
- Empty Recycle Bin.
- Reboot your computer.
Cyborg Ransomware Screenshots: