Mbed Ransomware Removal Guide
You might not understand what has happened when Mbed Ransomware invades your operating system, but soon after, you should discover that your personal files cannot be opened/read normally, and that is because the data within is encrypted. The process of encryption, as you might know already, is generally used to protect data against intruders, but in this case, intruders are locking personal files to ensure that their owners cannot access them. Cybercriminals are not interested in accessing your personal files, but they do not care if you ever get to access them yourself. What they care about is money, and they are hoping to extort some of it from you. To achieve this goal, they encrypt your files so that they could demand a ransom. According to the attackers, you can have your files fully decrypted if you pay some money. So, should you pay attention to the attackers, or should you delete Mbed Ransomware right away? We recommend initiating removal ASAP, but you can decide for yourself once you are done reading this report.
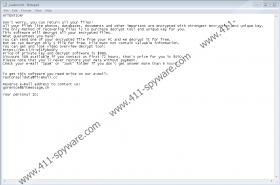
Mbed Ransomware is a clone of Nakw Ransomware, Toec Ransomware, Nols Ransomware, and hundreds of other infections from the STOP Ransomware. We even have reason to believe that most – if not all – of these threats are controlled by the same party. After infiltration, this malware encrypts files immediately, and the “.mbed” extension is attached to the files corrupted by Mbed Ransomware. A file named “_readme.txt” is dropped at the same time, and the message inside introduces victims to restorealldata@firemail.cc and gorentos@bitmessage.ch email addresses. The second one has been linked to most infections from the same family, and that is why we believe that we are dealing with the same attackers. The ransom note declares that files can be decrypted if the victim agrees to pay $490 (or $980 after three days) as the ransom. In return, an effective decryptor should be sent to the victim. Our research team does not believe that the attackers would offer a fair exchange, and since emailing them is risky too, we do not recommend doing even that. In conclusion, paying the ransom is not recommended.
In some cases, ransomware infections use encryptors that are decryptable. Mbed Ransomware belongs to the STOP Ransomware group, and the so-called STOP Decrypter exists. Whether or not you will be able to use it to restore your files, we cannot know. The tool certainly cannot decrypt every variant, and it appears to be capable of decrypting only those files that were corrupted using an offline key. Of course, you should try this tool out just in case it works. What if you have backups? If you have copies of your personal files (especially if they are stored outside of the infected computer), you do not need to consider paying the ransom, and you do not even need to worry about finding and applying a third-party decryptor. All you have to do is remove Mbed Ransomware and then replace the corrupted files with backup copies. Remember that removal must be performed first. Although it does not look like this infection could repeat encryption, we certainly do not want you to get your backups corrupted too. As long as malware is active, you need to be extra cautious. Of course, caution must be exercised even after you delete the threat.
It is believed that Mbed Ransomware could be spread via spam or using malicious bundled downloaders. Needless to say, if you open random emails or if you use unreliable downloaders, you could become a victim of a new file-encryptor – or a different kind of infection – before you know it. Therefore, once you remove Mbed Ransomware, you need to remind yourself to be cautious. When it comes to the removal of this dangerous threat, if you can locate the .exe file that launched it, you might be able to follow the instructions you can see below. Of course, we suggest employing anti-malware software instead. This software can guarantee that all threats are deleted fully and efficiently. Also, it can enable full-time protection in the future. If you secure your system, all you will need to do is create backups for the files you create in the future.
How to delete Mbed Ransomware
- If you can locate the launcher file, Delete it.
- Find the ransom note file _readme.txt and Delete it too.
- Launch Explorer by tapping Win+E keys.
- Enter %WINDIR%\System32\Tasks\ into the quick access field at the top.
- Delete the task called Time Trigger Task.
- Enter %LOCALAPPDATA% (or %USERPROFILE%\Local Settings\Application Data\) into the quick access field at the top.
- Delete the folder with a random name that contains a malicious {unknown name}.exe file.
- Launch Run by tapping Win+R keys and enter regedit into the dialog box.
- In Registry Editor, go to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run.
- Delete the value called SysHelper if it points to the {unknown name}.exe file in step 7.
- Empty Recycle Bin and then employ a trusted malware scanner to scan for potential leftovers.
Mbed Ransomware Screenshots: