Nvram Ransomware Removal Guide
Do you know what happens when you lose control over Windows security? Nvram Ransomware happens. This ransomware infection exploits RDP vulnerabilities and backdoors created by spam email and bundled downloaders to enter operating systems, and if they are unguarded, the malware slithers in seemingly without notice. It does not have an interface, and there are no windows or pop-ups that show up during the attack. The one thing that might signal the existence of this malware is the disabled Task Manager, but if you do not try to open the utility specifically, you will never know this. The threat disables Task Manager so that you could not terminate the malicious process responsible for encrypting files. Unfortunately, that means that you are unlikely to be able to delete Nvram Ransomware in time, even if you discover it. Needless to say, removal is important even after all files are encrypted.
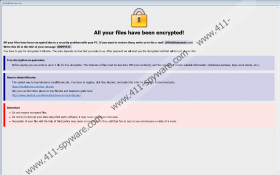
It is inaccurate to say that Nvram Ransomware encrypts all files because it avoids system files but, let’s be honest, those do not really matter. You can always replace system files and download applications. However, when it comes to personal files, they are not always replaceable. Do you have backups? If you do, you are in a good position because once you remove Nvram Ransomware, you can eliminate the corrupted files and replace them with backups. However, if you do not own backups – you are stuck. That is exactly what the attackers want. If you are stuck, they have the chance to trick you into paying money for an alleged decryption tool. This tool is introduced to victims using a message that is displayed on a window. This window is launched by Info.hta, a file created by the infection. Another file that this malware creates is called “FILES ENCRYPTED.txt,” and you are likely to find it on the Desktop. Without a doubt, we recommend deleting both the .hta and the .txt file from your operating system.
The message opened in a window is lengthier, and it includes information on how to purchase Bitcoins – which is the crypto-currency that the ransom is demanded in – and what not to do. The attackers behind Nvram Ransomware warn you not to rename files and not to use third-party software. In fact, if you rename the corrupted files (those with the “.id-{unique ID}.[clifieb@tutanota.com].nvram” extension), you are unlikely to hurt your chances of getting your files back because you are unlikely to have any chances at all. As for third-party software, a free Crysis/Dharma decryptor exists, but we cannot guarantee that they will be able to decipher the encryptor used by Nvram Ransomware. If you decide to employ this tool, make sure you are not tricked into downloading malware instead! What does this infection have to do with Crysis/Dharma Ransomware, you ask? This is the family that this malware belongs to along with 3442516480@qq.com Ransomware, RSA Ransomware, VIRUS Ransomware, and a ton of other threats. Note that individual removal guides for these threats have been posted on our website already.
In conclusion, if you decide to email clifieb@tutanota.com and then pay the ransom – which is what you are instructed to do – you are unlikely to get anything in return. The only thing that will change is that you will have less money in your hands. Hopefully, you can replace the files corrupted by Nvram Ransomware after deleting the threat, or you can employ a free decryptor that works. To eliminate the infection from your operating system, you have two main options. The first one is to find and delete all components manually. Most components of this threat are presented in the guide below, but we cannot know where the launcher file is. If you can find it, removing Nvram Ransomware manually is doable. If you cannot find it, install an anti-malware program to help you. We strongly advocate for the implementation of such a program because it can simultaneously remove infections and protect your system for the future.
How to delete Nvram Ransomware
- Find the launcher file, right-click it, and choose Delete.
- Find the FILES ENCRYPTED.txt file, right-click it, and choose Delete.
- Launch Windows Explorer (tap Win+E) and enter these pathsinto the field at the top one by one:
- %ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup\
- %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup\
- %APPDATA%
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\
- %WINDIR%\System32\
- If you can find them, right-click and Delete the Info.hta and {unique name}.exe files.
- Launch Run (tap Win+R) and enter regedit into the box to launch Registry Editor.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
- Right-click and Delete all values that point to the locations of Info.hta and {unique name}.exe files.
- Exit Registry Editor and Explorer and then Empty Recycle Bin.
- Perform a full system scan using a trustworthy malware scanner.
Nvram Ransomware Screenshots: