Deal Ransomware Removal Guide
Deal Ransomware is a malicious file-encrypting threat based on a similar harmful application called Phobos Ransomware. Both of them belong to the Crysis/Dharma Ransomware family, although they differ from other threats from this family with their colorful ransom notes. These notes should appear as soon as the malware finishes encrypting targeted files that ought to be marked with a unique second extension. If you want to know more about the way this new malicious application works, we encourage you to read the rest of this article. As for learning how to remove Deal Ransomware, you should not only finish reading our report but also check the deletion instructions located at the end of it. If you have any difficulties while erasing the malware or want to ask something about it, you could also use the comments section available at the end of this page.
One of the things you should learn about after receiving a threat like Deal Ransomware is how it might be spread. Such knowledge might help you avoid encountering malicious applications alike in the future. In most cases, such malware travels with Spam emails, or it is spread via P2P file-sharing networks and sources alike. Naturally, to make sure you do not get tricked into opening a malicious file unknowingly, we advise being cautious with Spam emails as well as messages from unknown senders. Also, it is recommendable to avoid visiting untrustworthy file-sharing websites, such as web pages that distribute torrents, unfamiliar freeware, and so on. Moreover, if you find it challenging to separate reliable sites or email from unreliable ones, you should get a reputable antimalware tool and use it to scan files received from the Internet. Additionally, it would be smart to keep your browser up to date as it might be able to alert you about questionable sites.
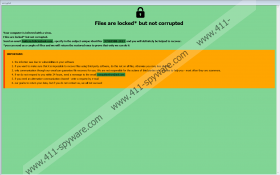
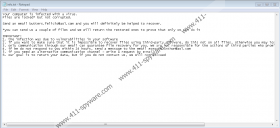
After slipping in unnoticed, Deal Ransomware should start encrypting documents, pictures, and other personal files located on an infected device. Such files should get a second extension that is partly unique to each infected device. As you see, it starts with a unique ID number and ends with .[butters.felicio@aol.com].deal, for example, .id[3C9E098B-2423].[butters.felicio@aol.com].deal. Later, the malware should create files called info.txt and Info.hta. Both of them ought to contain messages from the malicious application’s developers. However, the document should contain a shorter message than the .hta file. Info.hta might open a light green window with a black lock image. Most ransom notes of other threats from the Crysis/Dharma Ransomware family that start with: “All your files have been encrypted!” Nonetheless, the note (Info.hta) of Deal Ransomware should say: “Files are locked* but not corrupted.”
While it is true that the malicious application encrypts files, but does not damage them, they still become worthless without special decryption tools. Hackers behind Deal Ransomware offer to provide such tools to those who contact them via given email addresses. To convince victims that all will be well, they even offer to encrypt a couple of files. What you should know is that you will most likely be asked to pay for decryption tools. Sadly, even if you do pay a ransom, there are still no guarantees that cybercriminals will send you the needed decryption tools.
If your choice is not to put up with any demands, we advise not to wait any longer and erase this malicious application. To delete Deal Ransomware manually, you should complete the steps available below this paragraph. The other way to eliminate the malware is to scan your system with a reputable antimalware tool and wait till it provides a removal button.
Get rid of Deal Ransomware
- Tap Ctrl+Alt+Delete.
- Pick Task Manager.
- Select the Processes tab.
- Look for a process associated with the malware.
- Select the process and click End Task.
- Leave Task Manager.
- Tap Win+E.
- Go to these locations:
%TEMP%
%USERPROFILE%\Downloads
%USERPROFILE%\Desktop - Find the malicious file opened before the system got infected, right-click it, and select Delete.
- Navigate to these paths separately:
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup
%WINDIR%\System32
%APPDATA% - Search for files named Info.hta, right-click them and select Delete.
- Navigate to these paths:
%WINDIR%\System32
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup - Identify malicious executable files, e.g., file.exe; right-click them and choose Delete.
- Erase files called info.txt.
- Close File Explorer.
- Tap Win+R.
- Type Regedit and click Enter.
- Go to: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Identify the malware’s created value name, e.g., file.exe, right-click this value name, and press Delete.
- Locate this directory: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Find the malicious application’s created key, e.g., mshta.exe, right-click it, and select Delete.
- Close Registry Editor.
- Empty Recycle Bin.
- Restart the computer.
Deal Ransomware Screenshots: