Topi Ransomware Removal Guide
We might think they’re gone one day, but they make a comeback the next morning. We’re talking about ransomware infections, of course. Today, we bring you Topi Ransomware, which is one of the newest additions to the STOP Ransomware family.
What are we supposed to do with this infection? Remove it, of course. And while the manual removal isn’t that complicated, some users might feel discouraged to know that it is not always possible to recover the encrypted files. That’s why the prevention tactic is just as important as malware removal, when it comes to ransomware infections.
What can one do to avoid Topi Ransomware and other similar infections? We have to remember that the STOP Ransomware programs still keep on coming, and if you haven’t been infected with Topi Ransomware, you will most likely encounter MOOL Ransomware, Kodc Ransomware, BBOO Ransomware, and so on. All these programs employ the same distribution methods so, if you learn how to recognize a ransomware distribution tactic, you should be able to avoid Topi Ransomware.
These programs usually employ spam email attachments to reach their victims. It also means that users download and install the ransomware installer files willingly, even if they are not aware of that. How do these infections trick users into installing them? Well, the infection files often look like genuine documents. The spam email that delivered it might seem like an online shopping invoice or some financial report from a reputable company. If you do not look into it, it is only a matter of time before you open the file and infect your PC with Topi Ransomware. For that reason, it would be a good idea to scan all the received files with a reliable antispyware tool. It might slow down the file opening process, but at least you would protect your data from encryption.
On the other hand, if Topi Ransomware manages to enter your system, the program launches the encryption process almost immediately. All the affected files also receive an additional extension – “.topi.” This extension works like a stamp that says the files were affected by this malicious program. You will also notice that your system can no longer read the affected files, and all of their icons will change.
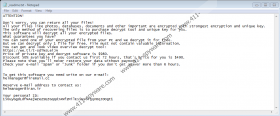
The program will also display a ransom note that says you have to pay if you want to get your files back. Here’s a short extract from the note:
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Is it true that you cannot restore your data without payment? It actually depends on many factors. If Topi Ransomware used the offline key to encrypt your files, you can decrypt them with the public decryption tool that works for several STOP Ransomware infections. If this program used a unique online key to lock up your files, things get tricky.
Of course, the best way to restore your files is to delete the encrypted copies, and transfer healthy files from a file backup into your computer. It might not be that easy if you do not keep a file backup, but you might have saved a lot of files in your inbox or on your mobile device, so there is always a chance that you have at least some of your files intact.
Also, please do not forget to remove Topi Ransomware for good, and then acquire a powerful security tool that will safeguard your PC against other dangerous infections in the future.
How to Delete Topi Ransomware
- Delete the most recent files from Desktop.
- Open the Downloads folder and remove the most recent files.
- Press Win+R and enter %HOMEDRIVE%. Press OK.
- Delete the SystemID folder and the _readme.txt file from the directory.
- Press Win+R and type %LOCALAPPDATA%. Click OK.
- Delete the folder with a long random name from the directory.
- Run a full system scan with SpyHunter.
Topi Ransomware Screenshots: