WANNACASH NCOV Ransomware Removal Guide
Windows operating systems that are not protected appropriately are at risk of being attacked by WANNACASH NCOV Ransomware, a malicious file-encrypting threat that was created to extort victims. The creator of this threat can exploit system vulnerabilities, use social-engineering scams, employ spam emails, conduct brute-force attacks, and utilize other methods to distribute it silently. Obviously, systems that are guarded should not let this malware in regardless of which attack method is used. However, if your operating system was not protected, you might be dealing with this malware already. Most likely, you live in a country, where the majority of people speak Russian, but new variants of this malware could emerge in the future, and they could be targeted at different users. In any case, deleting WANNACASH NCOV Ransomware is necessary, and even if your files do not get saved in the process, there is no time to waste. Removal is important.
Just like Jest Ransomware, Revon Ransomware, Npsk Ransomware, and other recently discovered file-encrypting threats, the malicious WANNACASH NCOV Ransomware was created to extort money. To succeed, this malware has to take something that belongs to users and then offer it back for something in return. In this case, the ransomware takes your personal files in return for money. The threat can encrypt .doc, .docx, .xls, .xlsx, .xlst, .ppt, .pptx, .accdb, .rtf, .pub, .epub, .pps, .ppsm, .pot, .pages, .odf, .odt, .ods, .pdf, .djvu, .html, .rtf, .1Cv8ddb, .1cl, .1CD, .cf, .dt, .efd, .jpg, .png, .mp4, .mov, .avi, .mpeg, .flv, .gif, .bmp, .3gp, .zip, .rar, .7z, .gzip, .gz, .tib, .bak, .iso, .dat, .cpp, .h, .pas, .dpr, .dproj, .py, .JS, .css, .php, .asm, .jar, .apk, .xml, .psd, .psb, .AEPX, .PRPROJ, .SWF, .veg, .txt, .bd, and .default files. This can cause a lot of damage because once videos, documents, photos, and other types of files are encrypted, the victim cannot read them. That basically means that the victim loses their personal files. This is done on purpose so that the attackers would have an easier time convincing victims to perform certain actions.
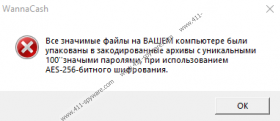
WANNACASH NCOV Ransomware uses a file called “как расшифровать файлы.txt” to explain what is expected from you. The message inside the file informs that files were encrypted using the AES-256 key, lists the affected extensions, and suggests sending two encrypted files so that they could prove that decryption is possible. You are meant to send them to noallpossible@cock.li, or to supermax@cock.lu if there is no response from the first one. It is stated that you have seven days to contact the attackers, after which, decryption will become impossible. So, what would happen if you contacted the attackers behind WANNACASH NCOV Ransomware? They would make you pay. This malware is identified as “ransomware” because the ultimate goal for the attacker is to make you pay money in return for your files. We cannot know exactly what the attackers would offer and promise, but know that their offers cannot be trusted and that their promises are empty. If you do not want to lose your money along with your files, you have to stay away from them. Moreover, emailing the attackers could be very dangerous because that could open the floodgates for other scams and other malicious infections.
If you are worried that you will not be able to find and remove WANNACASH NCOV Ransomware yourself, we have to warn that your worries are not unfounded. The launcher of this malware could be pretty much anywhere, and if you are not experienced, you might have a hard time identifying which file is malicious and which one is not. If you are worried that you could potentially delete something important instead of an actual malware file, why not leave the removal of WANNACASH NCOV Ransomware for anti-malware software? It is built to automatically erase malicious files, but that is not all. Its most important task is to secure you and your operating system against malware overall. If you think that you will be able to escape threats once you delete the ransomware, you are wrong. Unless you implement legitimate security software – which anti-malware software doubles as – you will never be safe. Another thing you should figure out is how to back up your files online or using external drives because if you have backups, you can replace corrupted files any time.
How to delete WANNACASH NCOV Ransomware
- If you can locate the launcher of the threat, right-click and Delete it (this file could be located on the Desktop, in the Downloads, in the %TEMP% directory, or another location).
- Right-click and Delete all copies of the как расшифровать файлы.txt file.
- Empty Recycle Bin and then quickly inspect your system for leftovers with the help of a malware scanner.
WANNACASH NCOV Ransomware Screenshots: