Sqpc Ransomware Removal Guide
You must have let Sqpc Ransomware into your Windows operating system by accident. Who would invite malware into their lives on purpose, right? Unfortunately, the attackers behind this malware are very sly, and they know how to trick more gullible and less cautious users into letting malware in. For example, they can create a misleading email message and attach the launcher as a document or photo attachment. The message could instruct to open the attachment to view flight/package/purchase/other important details. Once this file is opened – and usually macros has to be enabled – the infection executes silently. If security software exists on your system, the launcher should be detected and removed immediately. However, if your system is not guarded, the threat can freely encrypt your files, and deleting Sqpc Ransomware at that point might be too late. That being said, this threat must be eliminated, and it must be eliminated as soon as possible.
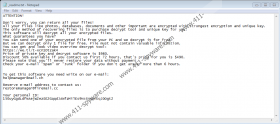
We know for a fact that Sqpc Ransomware is based off of STOP Ransomware, just like Jope Ransomware, Mpaj Ransomware, Toec Ransomware, and other well-known file-encrypting threats. They all add unique extensions to the files they corrupt (e.g., “.sqpc”), but other than that, they are identical. They all drop the exact same files in the exact same locations (in %HOMEDRIVE% and %LOCALAPPDATA%). The ransom note file used by all STOP Ransomware threats is called “_readme.txt,” and it always displays the same message. The only thing that changes is the contact details. However, even the email addresses repeat from one threat to the next, and so it is possible that we are dealing with the same attacker or group of attackers every time. Sqpc Ransomware lists helpmanager@mail.ch and restoremanager@firemail.cc as the email addresses that victims are supposed to send messages to. Victims are advised to send one encrypted file with the initial message, so that the attackers could prove that decryption is possible.
Even though the attackers behind Sqpc Ransomware might decrypt one file for free, they are unlikely to send you a decryption tool – which is what is promised – if you fulfill their demands. Once you contact them, they should immediately send you instructions on how to pay a ransom of $490 in return for a decryptor. However, if you do as told, you are unlikely to gain anything that you need. On the contrary, you are likely to be flooded with more misleading or intimidating messages, and your email address could be shared with other schemers, who might have different tactics to scam you or expose you to malware. Luckily, there are other options for you. First of all, do you have backups of personal files? If you have copies stored safely on external or virtual clouds online, all you need to do is use these copies to replace the corrupted files. You must remove Sqpc Ransomware first, however. Another option is to use the free STOP Decryptor that was created by malware experts. This tool cannot restore all files, but this is an option much better than the one offered by the cybercriminals.
We do not know if you can remove Sqpc Ransomware manually. That depends on whether or not you can identify malware files, and this could be difficult for those less experienced. On top of that, the removal of this dangerous infection is not the only thing to worry about. Other threats could exist on your system, and you also need to figure out how to overhaul Window security to prevent new attacks in the future. If you choose to delete Sqpc Ransomware manually (see guide below), you will need to figure out the removal of the potentially remaining threats and the protection of your system yourself. On the other hand, if you choose to install an anti-malware tool, your system will be cleaned and secured automatically. Only after all threats are erased should you use backups to replace the corrupted files, if this is the option you are choosing. In the future, always back up files to keep them safe, and do not forget that schemers can hide malware in the strangest places.
How to delete Sqpc Ransomware
- If you can identify the launcher of the threat, Delete it first.
- Launch File Explorer by tapping Windows+E keys on the keyboard.
- Enter %LOCALAPPDATA% into the field at the top to access the directory.
- Delete the [unknown name] folder with malicious [unknown name].exe file inside.
- Enter %HOMEDRIVE% into the field at the top of File Explorer.
- Delete the ransom note file named _readme.txt.
- Delete the folder named SystemID with the PersonalID.txt file inside.
- Exit File Explorer and immediately Empty Recycle Bin.
- Install a trusted malware scanner to examine your system for potential leftovers.
Sqpc Ransomware Screenshots: