HAT Ransomware Removal Guide
HAT Ransomware is a vicious threat that encrypts various personal files that could be located on an infected computer. The malicious application employs a robust encryption algorithm to encrypt targeted data, and, as a result, such data becomes unreadable. The only way to get the encrypted data back is to decipher it with special decryption tools. Unfortunately, a decryption tool that could restore files encrypted by this specific threat is not something that you can find on the Internet. The malware’s developers might have it, but they will likely ask you to pay a ransom before delivering the needed decryption tool. There are no guarantees that hackers would hold onto their promises. Thus, putting up with their demands may not be the best idea. If you wish to find out more about the malicious application, we encourage you to read the rest of this article. We can also offer our deletion instructions that show how you could erase HAT Ransomware a bit below this article.
If you wish to know how to avoid threats like HAT Ransomware, you should know how they are distributed. Our specialists say that hackers often send their victims email messages carrying malicious launchers that ask to open the attached files. Unfortunately, such attachments might look like text files, documents, or other file types that would not raise suspicion. Therefore, we recommend being cautious, even when you receive data that does not appear dangerous. If a file comes from an unknown source or arrives unexpectedly, it should be scanned with a reliable antimalware tool right away. A scan can determine whether a file is dangerous or not and, most importantly, prevent you from opening it. Of course, if you want to be as safe as possible, you should keep away from websites or spam emails that could distribute or contain malicious files, links, etc.
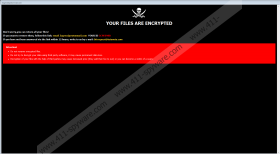
If HAT Ransomware enters a system, the malicious application should start encrypting files. Each file that gets encrypted ought to get a second extension that might be made from a unique ID number, hackers’ email address, and .HAT, for example, text.docx.id-6C7E098A.[Zagrec@protonmail.com].HAT. After encrypting files, the malware should create a text file with a short message that advises users to contact hackers via email. It should also open a pop-up window saying: “YOUR FILES ARE ENCRYPTED.” The pop-up should also contain a message saying that you can decrypt all of the HAT Ransomware’s locked files if you contact its developers via email. The difference between the message in the text file and the pop-up is that the later one suggests that users may have to pay to get decryption tools. To be more precise, the pop-up may say that it will cost much more to purchase decryption tools from third parties. As you probably understand, there are no guarantees.
Get rid of HAT Ransomware
- Tap Ctrl+Alt+Delete.
- Pick Task Manager.
- Select the Processes tab.
- Look for a process associated with the malware.
- Select the process and click End Task.
- Leave Task Manager.
- Tap Win+E.
- Go to these locations:
%TEMP%
%USERPROFILE%\Downloads
%USERPROFILE%\Desktop - Find the malicious file that was opened before the system got infected, right-click it, and select Delete.
- Navigate to these paths separately:
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup
%WINDIR%\System32
%APPDATA% - Search for files named Info.hta, right-click them and select Delete.
- Navigate to these paths:
%WINDIR%\System32
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup - Identify malicious executable files, e.g., file.exe; right-click them and choose Delete.
- Close File Explorer.
- Tap Win+R.
- Type Regedit and click Enter.
- Go to: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Identify the malware’s created value name, e.g., file.exe, right-click this value name, and press Delete.
- Locate this directory: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Find the malicious application’s created key, e.g., mshta.exe, right-click it, and select Delete.
- Close Registry Editor.
- Empty Recycle Bin.
- Restart the computer.
HAT Ransomware Screenshots: