GNS Ransomware Removal Guide
GNS Ransomware is a threat used to extort money from users who may accidentally infect their devices with it. After settling in, the malicious application encrypts all personal data and displays a ransom note that asks users to contact the malware’s developers. The message suggests that users would have to pay to get decryption tools to decrypt their files. No matter what the price could be, we advise not to pay it if you do not want to risk getting scammed. As you see, the hackers may prove that they have the needed decryption tools and promise to deliver them once they get the payment, but you cannot be sure that they will hold on to their end of the bargain. Thus, we advise you not to rush and learn more about the threat before deciding what to do. If you want to know how you could erase GNS Ransomware manually, you could check the deletion instructions located at the end of this text.
What we wish to discuss first is where GNS Ransomware could come from. Our specialists say that the malicious application belongs to the Crysis/Dharma Ransomware family and might be spread in the same ways as the threats that came before it. To be more precise, the malware could be distributed through unreliable file-sharing websites and spam emails. Thus, it means that if you want to avoid ransomware and treats alike, you should download software only from legitimate sources and be extra careful with emails from strangers. We should also mention that hackers’ emails might not raise any suspicion as they could pretend to be working for reputable companies. Thus, no matter where an email comes from, if you are surprised to receive it or do not know who sent it, we advise taking extra precautions. For instance, you could scan the attached file with a reliable antimalware tool or place your mouse pointer onto the attached link to see where it might take you.
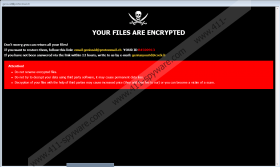
What if the malware gets launched? Sadly, you might not notice anything, and so GNS Ransomware could start encrypting your pictures, archives, and other personal files one by one. Each file that gets encrypted ought to get an additional extension named .GNS next to its title. For instance, a picture called clouds.jpg would become clouds.jpg.GNS. Next, the malicious application should create a text file containing instructions on how to contact them and open a pop-up window with the same instructions as well as additional information. For example, besides the hackers’ email addresses, the threat’s pop-up message might also say that asking third parties to help decrypt GNS Ransomware’s encrypted files would cost more. This explanation suggests that hackers offer to restore files in exchange for money. In such a case, users who write them might receive a message demanding to pay a particular amount of money.
As mentioned earlier, there are no reassurances that you will get the decryption tools. Thus, if you pay the ransom, you could lose your money in addition to losing your files. Provided you do not want to take any chances, we advise ignoring the malware’s ransom note. Also, it is vital to stress that if you have backup copies, you can replace encrypted files with them. Just make sure that you erase GNS Ransomware before doing so because if you do not, your files could get encrypted again. If you feel up to the task, you could try to get rid of the malicious application by completing the instructions located below. If the task seems too challenging, we advise employing a reliable antimalware tool to remove GNS Ransomware.
Get rid of GNS Ransomware
- Tap Ctrl+Alt+Delete.
- Pick Task Manager.
- Select the Processes tab.
- Look for a process associated with the malware.
- Select the process and click End Task.
- Leave Task Manager.
- Tap Win+E.
- Go to these locations:
%TEMP%
%USERPROFILE%\Downloads
%USERPROFILE%\Desktop - Find the malicious file opened before the system got infected, right-click it, and select Delete.
- Navigate to these paths separately:
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup
%WINDIR%\System32
%APPDATA% - Search for files named Info.hta, right-click them and select Delete.
- Navigate to these paths:
%WINDIR%\System32
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup - Identify malicious executable files, e.g., file.exe; right-click them and choose Delete.
- Close File Explorer.
- Tap Win+R.
- Type Regedit and click Enter.
- Go to: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Identify the malware’s created value name, e.g., file.exe, right-click this value name, and press Delete.
- Locate this directory: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Find the malicious application’s created key, e.g., mshta.exe, right-click it, and select Delete.
- Close Registry Editor.
- Empty Recycle Bin.
- Restart the computer.
GNS Ransomware Screenshots: