TEREN Ransomware Removal Guide
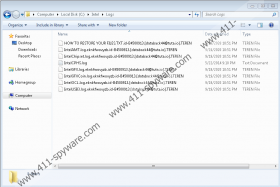
TEREN Ransomware is a new threat from the Crysis Ransomware family. Malicious applications that belong to this family often encrypt personal files that they mark with an additional extension made from a unique ID number, hackers’ email address, and a word or random characters. For example, files encrypted by this new variant ought to receive a second extension that might look like this: .id-D8944562.[databack44@tuta.io].TEREN. If a file gets encrypted, it becomes locked. The only way to unlock it is to decrypt it, but such a process requires special decryption tools. The malicious application’s developers might demand you to pay ransom to get them but keep it in mind that they might not hold on to their end of the deal. Meaning, they could scam you. If you want to learn more about the malware, we invite you to read our full report. We can offer our deletion instructions located below for users who want to know how they could remove TEREN Ransomware manually.
Users who want to avoid threats like TEREN Ransomware should know how they could be spread. Our specialists say that they might travel with spam emails or files from unreliable file-sharing websites. Thus, we highly recommend never interacting with links or attachments sent by people you do not know or for unknown reasons. In other words, if you are not expecting to receive a link or a file, you should take extra precautions. For example, you could scan the attached file with a reliable antimalware tool to learn whether it is malicious or not. Of course, we also recommend staying away from torrent and other file-sharing websites as they can contain installers that could be bundled with various malicious applications. It is safer to obtain needed installers from legitimate websites that you should go to by typing their address directly into your browser’s address bar. Also, we advise letting your system take care of updates. This way, you would not have to look for them yourself and risk ending up on a malicious website.
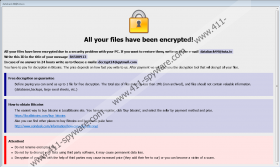
What does TEREN Ransomware do when it gets launched? At first, the malicious application should hide in the background until it finishes encrypting files. The malware seems to be only after photos, documents, and other files considered to be private, which is why it should leave data belonging to the operating system alone. Consequently, nothing should crash. However, users might notice that they cannot open their files. Nevertheless, by the time they see it, the malicious application could be already done. Once it encrypts files that it is after, TEREN Ransomware should open a pop-up window with a message from the threat’s developers. It ought to say that users can get their data back, but they need to pay ransom first. The note might say that the price depends on how fast users contact hackers. Nonetheless, we advise not to rush and think about your options carefully. Even though hackers may promise to deliver the needed decryption means, you cannot know for sure that they will hold on to such promises. In other words, they may not bother sending you the decryption tools even if you pay the ransom.
Of course, if you have backup copies, you might not need decryption tools because you might be able to replace all or most of the encrypted files. If you have backup copies or just have no wish to fund cybercriminals and risk getting tricked, we advise deleting TEREN Ransomware. If you think you are experienced enough, you could try to remove it manually. The instructions available below could be helpful, but you should know that we cannot guarantee that they will work for everyone. Another way to erase TEREN Ransomware from your system is to scan it with a reliable antimalware tool. After the scan, you could delete the malicious application and other identified threats by pressing the antimalware tool’s displayed removal button.
Get rid of TEREN Ransomware
- Tap Ctrl+Alt+Delete.
- Pick Task Manager.
- Select the Processes tab.
- Look for a process associated with the malware.
- Select the process and click End Task.
- Leave Task Manager.
- Tap Win+E.
- Go to these locations:
%TEMP%
%USERPROFILE%\Downloads
%USERPROFILE%\Desktop - Find the malicious file opened before the system got infected, right-click it, and select Delete.
- Navigate to these paths separately:
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup
%WINDIR%\System32
%APPDATA% - Search for files named Info.hta, right-click them and select Delete.
- Navigate to these paths:
%WINDIR%\System32
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup - Identify malicious executable files, e.g., file.exe; right-click them and choose Delete.
- Close File Explorer.
- Tap Win+R.
- Type Regedit and click Enter.
- Go to: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Identify the malware’s created value name, e.g., file.exe, right-click this value name, and press Delete.
- Locate this directory: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Find the malicious application’s created key, e.g., mshta.exe, right-click it, and select Delete.
- Close Registry Editor.
- Empty Recycle Bin.
- Restart the computer.
TEREN Ransomware Screenshots: