Npph Ransomware Removal Guide
We are sure that you understand the importance of deleting Npph Ransomware. This is a dangerous threat that might have invaded your Windows operating system without your notice. Unfortunately, you might have discovered it once the damage was done, and that damage is done to your personal files. At this point, the threat is unlikely to cause more problems, but it is an instrument of cybercrime, and you want it removed as soon as possible. Shouldn’t you figure out how to restore your files first? The truth is that we do not know if restoring files is possible at all. There is a free decryptor that, supposedly, can restore those files that were encrypted with an offline key. And you might also be able to replace the corrupted files without having to worry about decryption. In any case, the removal of the threat is important, and we hope that you are taking the matter seriously.
Our research team has seen many different versions of Npph Ransomware before. It all started with an infection called “STOP Ransomware.” Then, clones started to emerge, and the names of these clones usually consist of four or five letters. Most of them make absolutely no sense, such as Tabe Ransomware, Nppp Ransomware, Mosk Ransomware, or Kuus Ransomware. The names have to be random because there are literally hundreds of clones, and all names have to be unique. In fact, these names are not pinned by the attackers themselves. It is researchers who create these names by looking at the extensions that are appended to the corrupted files. Since “.npph” is the extension that is appended to the files that this particular STOP Ransomware variant corrupts, it is officially named as Npph Ransomware. Other than that, there are no visible differences between this variant and many others that were researched and removed before it. Even the ransom message is the same.
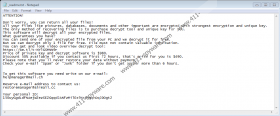
The first task for Npph Ransomware is to encrypt all personal files. The second task is to drop a file named “_readme.txt.” According to our research team, this file is dropped to %HOMEDRIVE%, along with a folder named “SystemID” that contains a file that should display a unique victim’s identification code. The message is standard, and it suggests sending “one of your encrypted file from your PC” so that the attackers could decrypt it for free. What is the point of that? The attackers hope to prove that decryption is possible, which should entice some victims to email helpmanager@mail.ch or restoremanager@airmail.cc (both of which have been seen in other variants’ ransom messages). If you do that, you might open a pandora’s box of scams and intimidating emails. Even if you want to pay $490 – which is the ransom that is supposed to be exchanged for a decryptor – know that the attackers are unlikely to aid you. Once they get your money, they are likely to move on. Unfortunately, at this point, no one can force cybercriminals to keep their promises. If that were possible, their cybercriminal activity would have been stopped already.
There are only a few components of Npph Ransomware that you need to delete from your operating system. Still, we do not know if you can identify them yourself. Obviously, if you cannot identify them, you might be unable to delete them, and you might even get yourself in trouble by deleting the wrong files. So, if you are not confident about your manual Npph Ransomware removal abilities, go for a different solution. We suggest implementing anti-malware software. This software is designed to automatically identify and remove all malicious components. And it also can help patch your system’s security cracks, which, hopefully, will keep new malware away in the future. Note that if you do not secure your operating system now, it could get infected by new threats before you know it. What happens after you are done with the threat? Hopefully, you can either employ STOP Decryptor (legitimate and free), or you can replace the files using copies that you created in the past.
How to delete Npph Ransomware
- Open File Explorer by tapping Windows+E keys at the same time.
- Type %LOCALAPPDATA% into the field at the top and hit Enter.
- Delete the {unknown name} folder that contains a malicious {unknown name}.exe file.
- Type %HOMEDRIVE% into the field at the top and hit Enter.
- Delete the folder called SystemID.
- Delete the file called _readme.txt.
- Empty Recycle Bin and then immediately install a reliable malware scanner.
- Run a system scan to check if there is anything else that you might have to delete.
Npph Ransomware Screenshots: