Epor Ransomware Removal Guide
Windows security is not some frivolous thing. If your system is protected, threats like Epor Ransomware should not stand a chance of invading it. However, if there is no security, every link you click, file you download, or spam email attachment you open could lead to the invasion of malware. Ransomware is very prevalent these days, but you must not forget about all other kinds of threats that could invade your system and do all kinds of terrible things as well. Some threats can steal passwords. Others can hijack and clean out your online banking accounts. Then there are threats that encrypt files. In most cases, files are encrypted so that attackers could demand ransom payments, and that is why these threats are known as ransomware. If you continue reading, you will find out how to delete Epor Ransomware. Note that there are more removal options than one, and we can discuss them all if you would like it.
What was the first sign of Epor Ransomware? If your system is not protected and equipped to remove malware before it is executed, it is unlikely that you noticed the ransomware establishing itself within your operating system. Most likely, you realized that something is wrong after discovering that your personal files (e.g., photos, archives, and documents) cannot be read and that the “.epor” extension is appended to the original names. This is a marker left by the attackers to help you assess the damage. The extension is what gave Epor Ransomware its name as well. This malware is part of the STOP Ransomware family, to which Foqe Ransomware, Mmpa Ransomware, Efji Ransomware, and other similar threats belong to as well. They are all clones, and the only difference is that they attach unique extensions to the corrupted files. Other than that, everything is the same, and we assume that the same attacker stands behind them all. Clearly, building hundreds of identical threats is a lucrative business.
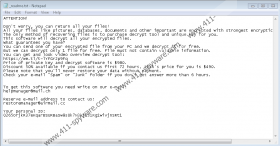
When Epor Ransomware encrypts files, it drops the “_readme.txt” file. The same file is dropped by all other clones, and the message inside is always the same as well. It is meant to convince that the only way to get the files back is to contact the attackers (at helpmanager@mail.ch and restoremanager@airmail.cc) and pay for a “decrypt tool and a unique key.” It appears that the full sum of the ransom is $980, but the message suggests that you can get a 50% discount if you act fast (three days). This might sound like a deal, but it is just another scam to get your money. The promise to give you a decryptor is likely to be a scam as well. As soon as you transfer the money, you are likely to find yourself empty-handed. On top of that, cybercriminals could make new demands and send you malware files if you expose yourself to them by contacting them. In general, this is not a good situation overall, and we suggest ignoring the ransom note. But what about the files? There is a free STOP Decryptor that might help, but we are sure that you can fix the situation only if you can replace the corrupted files with copies.
Did Epor Ransomware encrypt extremely important files? If it did, and they are the only copies you have, this malware can be extremely devastating. The attackers behind it might also have better chances at convincing you to pay the ransom, but remember that you must not expect anything from them, except for theft, scams, and treachery. If you have stored copies of your important files outside the infected computer, you have replacements, and you can use them after you remove Epor Ransomware. How do you remove this malware? One option is to do it manually, but we cannot point you to the threat’s components because we do not know where they are located. Another option is to pay for someone to deal with the mess professionally. Of course, we recommend installing anti-malware software that will automatically delete the threat and also secure your system. This is the best option at this time. If you want to discuss other options, post your comment below.
How to delete Epor Ransomware
- Delete the ransom note file named _readme.txt.
- Delete the {launcher name}.exefile. A few possible locations:
- %USERPROFILE%\Desktop
- %USERPROFILE%\Downloads
- %TEMP%
- Empty Recycle Bin and quickly install a trusted malware scanner.
- Scan the system and delete leftovers if they are found.
Epor Ransomware Screenshots: