8800 Ransomware Removal Guide
Most of us think that we are invincible, but 8800 Ransomware can change that in a matter of seconds. All it takes is to open the wrong email attachment, download the wrong file, or skip the wrong update, and a backdoor is open. The infection can slither in through it without notice, and then it can wreak havoc on your personal files. According to our researchers, this malware does not spare any personal files. While it does not touch system files, it is unlikely that you care much about those anyway. Unfortunately, this threat is one of thousands of file-encryptors that exist, and 8800 itself has clones, including Devil Ransomware, Dever Ransomware, or Bitx Ransomware, all of which derive from Crysis/Dharma Ransomware. If you face any of these threats, you need to be cautious, but in this report, we focus on one infection. Continue reading if you want to learn how to delete 8800 Ransomware and also secure your Windows operating system.
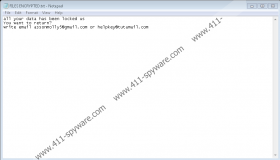
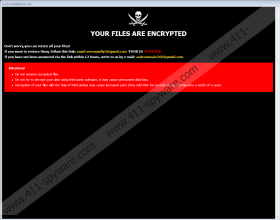
You might have learned that 8800 Ransomware invaded your operating system when the infection launched the “assonmolly5@gmail.com” window on your screen. A file named “Info.hta” is responsible for that, and the manual removal guide below shows how to remove it. Note that the file is also set up to launch on startup, and so you are bound to face the window even after you restart the computer. The window displays a message from the attackers, and it is meant to convince you to email them at assonmolly5@gmail.com or andrewseals560@gmail.com. 8800 Ransomware also drops a file named “FILES ENCRYPTED.txt,” and the message represented via this file asks to email assonmolly5@gmail.com or helpkey@tutamail.com. Of course, we do not recommend sending a message to either one of these addresses. Why? That is because cybercriminals are on the other end, and they can scam you. First, they would ask you to pay a ransom in return for a decryptor, and that is a demand you do not want to give in under any circumstances.
When your files are encrypted and the “.id-*.[assonmolly5@gmail.com].8800” extension is added to them, they become unreadable due to the changes within the data. The attackers who created the encryptor should have a matching decryptor, and so they are the ones who can restore your files; however, that does not mean that they would. Our research team has analyzed thousands of file-encryptors at this point, and most of them have similar traits. First of all, they use vulnerabilities and backdoors to slither in. Second, they target personal files. Third, they ask for money in return for decryptors. Finally, they do not give decryptors after the payments are received. Due to this, we do not recommend interacting with the attackers behind 8800 Ransomware or paying the ransom, even if it is small enough for you to take risks. We hope that you can replace the lost files with backups copies or that you can successfully employ Dharma Decryptor or Crysis Decryptor. Unfortunately, at the time of research, we could not confirm that these tools actually restore the files corrupted by 8800 Ransomware. If you decide to install them, be careful.
Do you have any experience with the removal of malicious files? If you do, you know that, in some cases, they might have unique locations and unique names. That is the case with 8800 Ransomware, whose launcher could be anywhere. If you cannot find and delete this file, following the instructions posted below will not help you much. In that case, we advise leaving the removal of 8800 Ransomware up to anti-malware software. If you implement software that is legitimate, up-to-date, and reliable, you will have the threat deleted and your operating system secured in no time. Note that eliminating the PUP is just one part of the job. If you want to ensure that no one invades your system and tries to harm your files again, you need to take care of your security, and anti-malware software was designed for that. If you want to ask us questions about the threat or its removal, use the comments section below.
How to delete Removal
- Right-click and Delete the .exe file that executed the ransomware.
- Right-click and Delete the FILES ENCRYPTED.txt file (check the Desktop).
- Launch File Explorer (tap Win+E keys) and enter the following pathsinto the field at the top one by one:
- %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup\
- %ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup\
- %APPDATA%
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\
- %WINDIR%\System32\
- If you find Info.hta and {unknown name}.exe files, right-click and Delete them.
- Launch Run (tap Win+R keys) and enter regedit into the box to launch Registry Editor.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
- Right-click and Delete all values (should be three) that are linked to Info.hta and {unknown name}.exe files.
- Empty Recycle Bin and then quickly install a trustworthy malware scanner.
- Perform a full system scan to check for potential leftovers.
8800 Ransomware Screenshots: