Afrodita Ransomware Removal Guide
No one wants to get infected with the likes of Afrodita Ransomware, but not everyone knows how to avoid ransomware. The truth is that there is no secret: We all just need to be more attentive when we download new unfamiliar files. In this entry we shall tell you more about Afrodita Ransomware, and we will look at the ways we can recognize ransomware distribution patterns. After all, it is often very hard to restore the files affected by a ransomware encryption, so it is always recommended to focus more on prevention rather than removal.
We actually know how the file that infects computers with Afrodita Ransomware is called, which is not that common when it comes to ransomware research. The file that carries the infection poses as an invoice document. If you often deal with online shopping and other types of invoices, be careful when you open new messages from unfamiliar senders. The file that launches the infection is called Invoice.xlsm (note the file format). And the infection slithers into the target system through a VBS macro that is in the file. It also means that you have to have your macros enabled for Afrodita Ransomware to enter your system.
An interesting thing is that the Invoice.xlsm file does look like an invoice when you open it. And it also displays information entirely in the Polish language. Hence, there is a good chance that Afrodita Ransomware mostly targets users in the Central Europe. At the same time, the main targets of this infection are probably business entities rather than individual users. After all, businesses are more likely to transfer the ransom payment, especially if they do not have copies of their important data.
When the infection process is launched the malicious files downloads the actual payload on the compromised system. The payload is downloaded as a JPG format file, but the system saves it at Afrodita.dll, and then the malicious DLL is executed. This allows Afrodita Ransomware to launch properly, and then the infection encrypts extensive lists of your files. However, we have also found that there are certain directories that the program skips during the encryption process. These directories include: Program Files, Program Files (x86), Windows, AppData, ProgramData, and All Users.
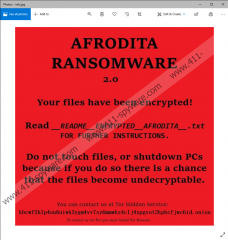
This program also drops a ransom note in every folder that was affected by the encryption. Aside from that, it may also open an info.jpg file when the encryption is complete. This file contains the summarized information about what happened to your PC. Here’s what it says:
AFRODITA RANSOMWARE 2.0
Your files have been encrypted!
Read __README__ENCRYPTED__AFRODITA__.txt FOR FURTHER INSTRUCTIONS.Do not touch files, or shutdown PCs because if you do so there is a chance that the files become undecryptable.
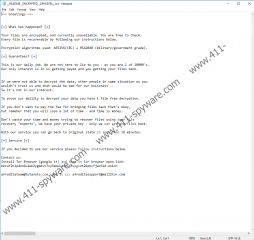
You can contact us at Tor Hidden Service:
[Tor Hidden Service address]
To contact us via Tor you must install Tor Browser.
Although some companies may choose to contact these criminals and pay the ransom fee, it is not a wise decision. Of course, it’s a relief to you and your business if these criminals do issue the decryption code that helps you restore your files, but that is very unlikely.
If you have the money to spare for these criminals, it’s better to address professional technicians instead. At the same time, you will be able to learn more about ransomware infections, and with this new knowledge, it would be a lot easier to avoid similar intruders in the future.
Also, do not forget to create a file backup because ransomware is always waiting for the opportunity to invade vulnerable systems. If you have copies of your files saved somewhere else, at least half of the potential problems are pushed off your shoulders.
How to Remove Afrodita Ransomware
- Press Win+R and the Run prompt will open.
- Type %APPDATA% into the Open box and click OK.
- Remove the info.jpg file from the directory.
- Use SpyHunter to run a full system scan.
Afrodita Ransomware Screenshots: