Ahegao Ransomware Removal Guide
When did Ahegao Ransomware invade your Windows operating system? You might have no answer to this question because it is very stealthy, and you are not supposed to discover it upon execution anyway. That being said, you might remember downloading some strange file, opening an odd spam email attachment, following an unfamiliar link, or perhaps skipping an update. All of these actions could help cybercriminals exploit your virtual security and drop malware. If this is what has happened, your personal files must be encrypted. The “.ahegao” extension is automatically attached to the files that get encrypted, but the main issue lies not within the names but within the data of the files. It is ciphered in a way that only those with a decryptor can open the files normally. That is what the attackers are offering the victims of the infection. Unfortunately, whether you pay the ransom for the decryptor or delete Ahegao Ransomware instantly, your files are likely to be stuck forever.
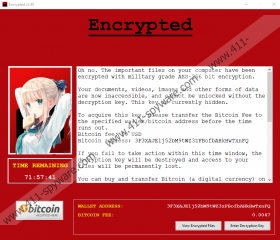
You might have no idea how Ahegao Ransomware got into your operating system, and you are not supposed to notice when that happens. However, once this malware is ready to take off the mask, you are bound to notice it right away. Once the infection encrypts all personal files found on your operating system, it immediately launches a window entitled “Encrypted v2.40.” The same file that launched the infection is also responsible for launching this window. In fact, it appears that no other file is dropped by the threat, which might make the manual removal of Ahegao Ransomware quite straightforward. That is if you can find the launcher of the infection yourself. The window displays a timer and a message. According to it, you have 72 hours to pay a ransom of 50 US Dollars in return for a decryption key that, allegedly, is the only thing that can “unlock” your personal files. This is not a huge ransom, but you are supposed to pay it in Bitcoin, which not all users know how to do. The Bitcoin wallet address to which the payment has to be made is 3F3XAJE1j52bM9tWZ3zFBofbAHkHwTxnFQ, but when we checked it, no one had transferred any money to it. This is great news.
After you pay the ransom – and we hope that you choose not to take the risk – you are also supposed to send an email to l33tsupp0rt1337@protonmail.com. If you pay the ransom, you are unlikely to get anything in return for your money. If you contact cybercriminals, they could try to scam you in other ways. Even if the launcher of Ahegao Ransomware was introduced to you via a clever spam email, cybercriminals usually distribute malware launchers blindly. That means that they take a list of publicly available email addresses and they just send a misleading message en masse. However, if you contact the attackers directly, they will know for sure that they are dealing with a real person, and they could use this opportunity to expose you to phishing scams, sextortion, and other awful things. Furthermore, your email address could be shared with other attackers, who could try to send you emails with new malware launchers. This is why we do not recommend paying the ransom or contacting the attackers behind Ahegao Ransomware.
If you have backups or copies of your personal files, you do not need to be afraid of the demands made by the Ahegao Ransomware creator. All you have to do is delete this infection and then replace the corrupted files with backups/copies. Of course, it matters where your copies are. If they are stored within your computer, they are likely to be lost. On the other hand, if you have stored them online or on external drives, you should be good to go. First, however, you need to remove Ahegao Ransomware. As we mentioned earlier, there is only one file to delete, and if you can find it, you should be able to perform the manual removal successfully. However, we recommend that you implement anti-malware software instead. Not only will it delete the infection automatically but will also secure your Windows operating system, which is what you need if you want to keep new threats away in the future.
How to delete Ahegao Ransomware
- Locate the {unknown name}.exe file that launched the threat.
- Right-click the malicious file and choose Delete.
- Empty Recycle Bin once you think that malware was erased.
- Scan your system for other malware components using a trusted malware scanner.
- Remove any leftovers that could be found.
Ahegao Ransomware Screenshots: