.bip File Extension Removal Guide
The .bip File Extension ransomware is a malicious program one may encounter after opening infected files received via email or downloaded from doubtful file-sharing web pages. After its launch, the malware should start the encryption process, during which all user’s pictures, documents, videos, and other personal files are supposed to be encrypted. It means the data would become unrecognizable and the user should be unable to open it. Once all targeted files are ruined, the malicious program might drop a ransom note asking to write its creators to the given email address. At this point, we would like to warn you, doing so could result in hackers asking you to pay a ransom. Keep it in mind, despite what they promise, in the end, they might not be willing to help you, and all the invested money could be wasted for nothing. Therefore, we highly recommend not to deal with the .bip File Extension ransomware’s creators and erase the infection with our prepared deletion instructions located below.
The moment the user launches a file carrying the .bip File Extension ransomware the malware should create a couple of copies of it in the %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup and %WINDIR%\System32 locations. Such data might be named the same way as the malicious program’s installer, although the titles could be random as well. Next, the threat is supposed to access the HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run path where it should create value names titled again similarly to the installer or randomly. Usually, the value names in the Run key are designed to enable the software launch itself or some file automatically with the operating system. Thus, we believe it is possible the .bip File Extension ransomware might be launched over and over again when the computer gets turned on. As a consequence, the already encrypted files should be enciphered once again; plus, it could ruin all the data the user may create afterward.
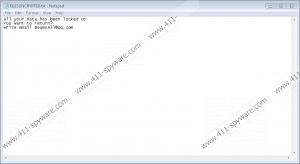
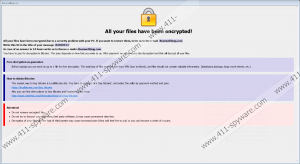
Furthermore, our specialists who tested the .bip File Extension ransomware say it should add a rather long and unique extension to each encrypted file, e.g., .id-B4500913.[Beamsell@qq.com].bip. Sadly, there is nothing one can do to files that have this extension without a unique decryption key and a decryptor. To make matters worse, it looks like the malware was programmed to eliminate all Shadow copies, making it impossible to recover any files. On the other hand, if you prepared a backup, you could switch encrypted files with their copies, although before accessing backup it would be smart to remove the .bip File Extension ransomware first if you do not want to risk losing it too. What we advise against is contacting the malware’s developers as it should be requested in the ransom notes (Info.hta and FILES ENCRYPTED.txt), because you might end up losing your money in vain. After all, there is not knowing whether the malicious program’s creators have decryption tools or would send them to you.
For users who do not wish to risk their savings or endanger the data they might still create or place on the infected computer; we advise getting rid of the .bip File Extension ransomware. Those of you who would like to try erasing it manually could use the recommended removal steps located at the end of this text. Naturally, if the task looks a bit too complicated, you could get a reliable security tool instead, scan the device with it, and then remove the malicious program by pressing the given deletion button.
Get rid of the .bip File Extension ransomware
- Tap Ctrl+Alt+Delete.
- Select Task Manager.
- Locate a particular process belonging to the malware.
- Mark it and press End Task.
- Exit Task Manager.
- Press Win+E.
- Locate the given directories:
%TEMP%
%USERPROFILE%\Desktop
%USERPROFILE%\Downloads - Find a malicious file downloaded before the infection appeared.
- Right-click the doubtful file and select Delete.
- Then find these locations:
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%WINDIR%\System32 - Look for malicious executable files with random names or titles similar to the threat’s installer.
- Right-click them and select Delete.
- Locate the ransom notes: Info.hta and FILES ENCRYPTED.txt.
- Right-click them and press Delete.
- Exit File Explorer.
- Press Win+R.
- Type regedit and press Enter.
- Navigate to: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Look for suspicious value names created by the malware.
- Right-click these value names and press Delete.
- Exit Registry Editor.
- Empty your Recycle Bin.
- Reboot the system.
.bip File Extension Screenshots:
.bip File Extension technical info for manual removal:
Files Modified/Created on the system:
| # | File Name | File Size (Bytes) | File Hash |
|---|---|---|---|
| 1 | Dharma.exe | 341575 bytes | MD5: b84e41893fa55503a84688b36556db05 |
| 2 | Info.hta | 13910 bytes | MD5: 8d2c8d4b866434e3955ad4ce30869ca8 |
| 3 | FILES ENCRYPTED.txt | 164 bytes | MD5: b1016794f99f2896abf3f2a3f75980dc |
Memory Processes Created:
| # | Process Name | Process Filename | Main module size |
|---|---|---|---|
| 1 | Dharma.exe | Dharma.exe | 341575 bytes |

