Bmtf Ransomware Removal Guide
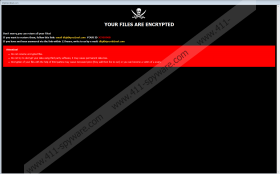
Bmtf Ransomware is an infection that encrypted your personal files and added the “.id-{unique ID code}.[dfgkbtprz@aol.com].bmtf” extension to their names. Documents, videos, photos, and other files are not off-limits for this malicious infection. In fact, it is only interested in personal files because that increases the chances of backing you into a corner. If you do not have copies of all personal files stored somewhere outside the infected system, you might be more willing to pay the ransom that the attackers are likely to request in the end. First, you are supposed to establish communication with them, and we hope that you have not made this mistake yet. There is a chance that you can recover all files even if you do not have copies backed up. That being said, while we cannot guarantee full decryption, we can assure you that you can delete Bmtf Ransomware from your operating system.
Bmtf Ransomware is not much different from WCH Ransomware, NCOV Ransomware, SySS Ransomware, and numerous other infections that were created by cybercriminals who use the same malware code. The predecessor is Crysis Ransomware, or Dharma Ransomware, and that is the name that your malware scanner might identify Bmtf Ransomware by as well. There are literally hundreds of threats that were created using the same code, which is why researchers had the opportunity to dedicate more attention to the family. In the end, a free decryptor was created. Can you use it to restore the files that were corrupted by the Bmtf variant? We hope so, but please make sure that you do not install some dupe that was built by cybercriminals. The demand for this tool is high, and cybercriminals can use that to their advantage. Of course, before you install anything new, it is a good idea to look through your backups (use a malware-free computer for that), and if you have copies, you can rely on them. Before you start replacing the corrupted files, you must remove the infection.
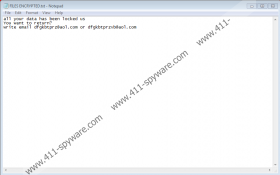
The attackers behind Bmtf Ransomware are hoping that you do not learn about the free decryptor and that you do not have copies of personal files. That is the only way they can scam you. “Info.hta” and “FILES ENCRYPTED.txt” files are dropped by the threat to introduce you to two different ransom notes. They both suggest sending emails to dfgkbtprz@aol.com or dfgkbtprzvb@aol.com. If you decide to contact the attackers, you must use a new email account because you will want to remove it afterward. If you use your normal email account to communicate with cybercriminals, they could flood you with misleading emails, and that could lead to the invasion of new infections. As it turns out, Bmtf Ransomware itself is most likely to spread with the help of spam emails and RDP vulnerabilities. All in all, if you have no intention of paying a ransom to cybercriminals, there is no point in sending an email. Note that if you cannot use the free decryptor or replace the files, you should not pay the ransom anyway because the attackers cannot be forced to give a legitimate decryptor in return for it.
Can you name all components of Bmtf Ransomware? If you cannot, you might be unable to delete this threat manually. The good thing is that you do not have to. If you want to give this option a try, follow the instructions below, but do not forget to scan your system afterward to check whether your system is clean or if you need to delete malware leftovers. Alternatively, you can install automated anti-malware software, and this is what our research team recommends doing. Not only is this software built for automated Bmtf Ransomware removal but also can secure your entire operating system against malware attacks, which is crucial if you want to stay safe in the future. Is this enough to ensure the complete protection of personal files? New threats emerge daily, and some of them are more powerful than others. Unfortunately, no security tool can guarantee 100% protection, which is exactly why you also want to back up all personal files just in case. As long as you have a file and its copy in different places, you should be fine even if malware finds a way in again.
How to delete Bmtf Ransomware
- Open File Explorer by tapping Win+E keys simultaneously.
- Enter the following lines into the bar at the top (one by one) and Delete the file named Info.hta and a malicious {random name}.exefile if you can identify it:
- %ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup\
- %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup\
- %APPDATA%
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\
- %WINDIR%\System32\
- Open Run by tapping Win+R keys simultaneously.
- Enter regedit into the dialog box and click OK.
- In Registry Editor, move to HKLM \SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
- Empty Recycle Bin and then immediately employ a trusted scanner to perform a full system scan.
Bmtf Ransomware Screenshots: