Cerber Ransomware Removal Guide
A new dangerous ransomware has emerged, and it is known as Cerber Ransomware. This devious threat is a danger to everyone except those living in Armenia, Azerbaijan, Belarus, Georgia, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Turkmenistan, Ukraine, and Uzbekistan. This list is stored in a configuration file that also contains information regarding the files that must be encrypted or ignored. It was found that this ransomware is incapable of encrypting files in your Recycle Bin, Program Files directory, or the Tor Browser folder. Needless to say, this infection does not need to encrypt your system files because they can be replaced and because that might stop you from following the demands presented by the creator of this ransomware. One of these demands is to download Tor Browser because your interaction with cyber criminals via it allows them to stay concealed. Unfortunately, whether or not you follow the demands, you will have to delete Cerber Ransomware.
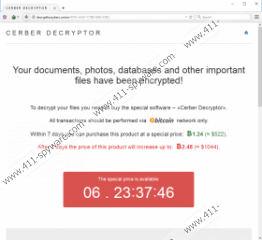
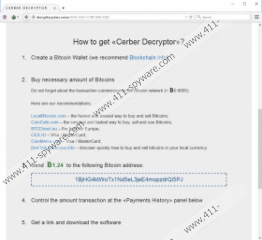
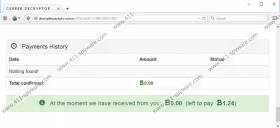
Cerber Ransomware is similar to Hi Buddy Ransomware, Crysis Ransomware, and all other computer threats that we categorize as ransomware. These threats slither into computers, use different encryption methods to encrypt personal files, and then demand ransom payments. The ransom requested by this malicious infection is 1.24 bitcoins, which, at the moment is $507. Users are warned that the ransom might double (2.48 bitcoins) if not paid within 7 days. This warning is shown in a page served via decrypttozxybarc.onion. A link to this page is provided in “# DECRYPT MY FILES #.html” and “# DECRYPT MY FILES #.txt” files that can be found in every location where files with the .cerber extension – which indicates that the file is encrypted – are found. There is another file that warns computer users, and it is called “# DECRYPT MY FILES #.vbs”. This file uses Narrator to “read” the warning out loud. This file contains a script that looks like this:
Set SAPI = CreateObject("SAPI.SpVoice")
SAPI.Speak "Attention! Attention! Attention!"
For i = 1 to 5
SAPI.Speak "Your documents, photos, databases and other important files have been encrypted!"
Next
Unfortunately, Cerber Ransomware uses AES and RSA encryption (AES for files and RSA for the private key) to make the decryption of files impossible without paying the ransom. Since this threat encrypts photos, PDF files, documents, audio and video files and other types of files that we would consider personal, many users are likely to pay the ransom. Can cyber criminals be trusted to hold their end of the deal and decrypt files once the ransom is paid? Unfortunately, we cannot predict that, but trusting cyber criminals and their intentions is always risky. Of course, if you simply must decrypt the files, you might have to take a risk. First, we suggest looking into third-party decryption tools. At the moment, tools that could decrypt Cerber Ransomware do not exist, but if you find them in the future, make sure you are not getting scammed. Speaking of scams, how did this ransomware get onto your PC? Was it installed by other malicious programs? Did it conceal itself as a spam email attachment? Was it installed in some other way? It might be difficult to figure this out, considering that the ransomware always remains quiet. If it was not quiet, you could have a chance to delete it before the encryption began.
Paying the money to schemers is the last resort, and we are hopeful that you will not need to do that. In either case, even if you pay the ransom, you must remove Cerber Ransomware from your operating system, and this operation is not that simple. The most difficult thing is identifying malicious files and values because they might have random names, or maybe even names that do not look suspicious at all. We can provide you the locations and registries where this ransomware is likely to be found, but it is up to you to figure out which files or values you need to eliminate. If you cannot perform the steps below yourself, you can install an automated malware remover to erase all existing threats. Unfortunately, the malicious ransomware could be running on your operating system along with other infections, and, of course, they require removal as well. In this case, an automated malware remover is the right tool to use.
How to delete Cerber Ransomware
- Simultaneously tap Win+E to launch Explorer.
- Enter %AppData% into the address bar. This is the main location of the infection.
- Delete the folder with a random CLSID name.
- Delete the shortcut files ([random name].lnk) that can be found in these directories:
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\
- %ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\
- %ALLUSERSPROFILE%\Start Menu\Programs\
- %USERPROFILE%\Microsoft\Windows\Start Menu\Programs\
- %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\
- Simultaneously tap Win+R keys to launch RUN.
- Navigate to HKEY_CURRENT_USER\Control Panel\Desktop.
- Delete the value SCRNSAVE.EXE ( value data is %AppData%\{RANDOM CLSID}\*.exe).
- Navigate to these paths and Delete values with random names (value data might look something like this: %AppData%\{RANDOM CLSID}\*.exe):
- HKEY_CURRENT_USER\Software\Microsoft\Command Processor\AutoRun
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Cerber Ransomware Screenshots: