Copa Ransomware Removal Guide
If you are currently dealing with Copa Ransomware, we have to warn you about one thing right off the bat, and that is that cybercriminals are hoping that you will cave in. They have created this malicious threat to make money, and they are hoping to achieve that by taking your files hostage. The attackers do not remove your files or hide them somewhere you cannot find them. Instead, they use an encryption key to lock them. Unfortunately, only a matching decryptor can guarantee full decryption. Since that is what you need, the attackers are quick to offer a decryptor for you. That being said, it is clear that all they want is money, and it is highly unlikely that they would ever put in the work to help their victims. So, what does that mean? Are you doomed to lose your files? Should you risk paying the ransom? Should you look for other decryptors? Should you dedicate your time to delete Copa Ransomware? These are the questions that are answered in our report.
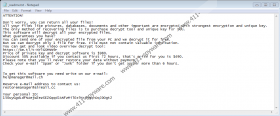
Do you remember letting Copa Ransomware in? Most likely, you do not. However, you might be able to trace your steps back and, at least, think of when this malware could have slithered in. Perhaps you remember opening a strange email attachment? Perhaps you have recently downloaded an update that you were introduced to via some website? Perhaps you downloaded new software or files? Although exploits and other threats can be used to execute Copa Ransomware, cybercriminals are often relying on sneaky infiltration tactics, and victims are often involved. The truth is that the attackers behind this particular ransomware are already experienced with malware distribution because they are responsible for Tabe Ransomware, Kuus Ransomware, and hundreds (literally) of other threats that are clones of the infamous STOP Ransomware. They are identical from head to toe, so to speak, and even the ransom note is always the same. It is represented using a file named “_readme.txt,” and the message is meant to convince you that only the attackers can provide you with a working decryptor. Well, even if they have a decryptor, who can guarantee that they would share it?
The files that Copa Ransomware encrypts are not renamed, but the “.copa” extension is added as a marker to help you identify the corrupted files. You can even delete this extension if you want to. Of course, that will not help you restore the files. Removing Copa Ransomware will not help either. There are, however, a few things that might help. First of all, perhaps you do not need to worry about decryption at all? If you have copies that are stored outside the computer, you can use them to replace the encrypted files. If that is possible, perform the replacement only after you remove the infection. Another option to consider is using a free decryptor. In most cases, ransomware victims cannot use free decryptors, but there is one specific tool (STOP Decryptor) that was created for the victims of STOP Ransomware. It is important to note that this tool was NOT specifically created for Copa, and so it cannot guarantee full decryption. What about paying the ransom in return for a decryptor that the attackers are offering? Since we do not believe that cybercriminals’ promises can be trusted, we do not recommend paying the ransom or even contacting them via helpmanager@mail.ch and restoremanager@airmail.cc.
Whether you pay the ransom or not, whether you are able to replace your files or not, whether you can use a free decryptor or not, removing Copa Ransomware is mandatory. This malware does not belong on your Windows operating system, and the sooner you get rid of it, the better. If you want to, you can try deleting this malware manually, and we have created a manual removal guide that might be helpful. However, if you want to have the threat erased automatically, your system scanned for other threats, and also reliable full-time protection against malware enabled, we advise installing anti-malware software. Of course, even if your system is protected, you must not forget to install updates, ignore spam emails, download from reliable sources only, and, of course, always create copies of important files.
How to delete Copa Ransomware
- Open File Explorer by simultaneously tapping Windows and E keys on the keyboard.
- Enter %HOMEDRIVE% into the quick access field at the top to access the directory.
- Right-click and Delete the _readme.txt file and the SystemID folder.
- Enter %LOCALAPPDATA% into the quick access field at the top to access the directory.
- Right-click and Delete a folder that contains an .exe file. The name of the folder is random (e.g., 0115174b-bd55-4caf-a89a-d8ff8132151f), and the file inside has a unique name also.
- Once you Empty Recycle Bin, immediately perform a system scan using a legitimate malware scanner.
Copa Ransomware Screenshots: