Coronavirus Ransomware Removal Guide
The Coronavirus disease is drawing attention from many things, including cybersecurity, which is why it is no wonder that hackers find the timing to be perfect to release new threats like Coronavirus Ransomware. Our specialists say that it is a tool for money extortion since it encrypts files on an infected device to take them as hostages and then shows a ransom note containing instructions on how to pay ransom to get files decrypted. If you come across this malware, we recommend reading our full report to get to know it better. Also, we advise not to leave it unattended and erase Coronavirus Ransomware with a selected antimalware tool that you trust or use the removal instructions located at the end of this page.
Users who are encountering a threat like Coronavirus Ransomware for the first time, might be interested in its distribution. Our specialists say that most of such malicious applications travel with malicious emails, software installers, pop-ups, and content alike. For example, users could receive it after opening an infected email attachment, launching a harmful installer, or interacting with a fake notification.
Thus, it is extremely important not to interact with content that could be unreliable if you do not want to get tricked into launching threats like Coronavirus Ransomware. Hackers could try to convince you to open malicious files or links by saying that they could be of great use to you or that they are important and must be reviewed right away. For example, hackers behind this ransomware could say that their installers will show the map of Coronavirus or other useful information related to it. To avoid being tricked like this, we advise you not to trust strangers and scan data from the Internet with a reliable antimalware tool before opening it as well carefully research received links or pop-ups to confirm that they are legit. Plus, it would be safer if you had a reliable antimalware tool on your system that could stand guard.
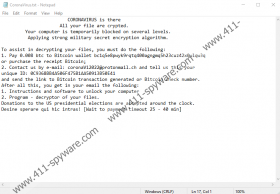
There is not that much to say about Coronavirus Ransomware’s working manner. It appears that the application does not drop any files upon it entering a system. Therefore, it could be working from the directory where it was downloaded and launched. After its launch, it ought to start encrypting various documents pictures, and other files that its victims’ might not want to lose. Next, the malicious application should create a text file called CoronaVirus.txt. Inside of this document, victims should find a message saying that files can be decrypted only if they pay 0.008 BTC, which is a bit more 50 US dollars (at the moment of writing) to the malware’s creators. In exchange, hackers promise to deliver decryption tools.
There are no guarantees that Coronavirus Ransomware’s developers will do as they promise. In other words, they could take your money without delivering the promised decryption tools, in which case, you would end up losing not just your files. If you do not want to risk getting scammed like this, we advise you not to pay ransom. If you have backup copies you could replace encrypted files with such copies, in which case, you might not need any decryption tools. Of course, we advise removing Coronavirus Ransomware first as it could still pose a threat. To get rid of it manually, you could try the instructions located below. If you prefer using security tool, we recommend erasing it with a reliable antimalware tool of your choice.
Get rid of Coronavirus Ransomware
- Tap Ctrl+Alt+Delete.
- Pick Task Manager.
- Check the Processes tab and identify a process belonging to the malicious application.
- Choose it and press the End Task button.
- Close Task Manager.
- Press Win+E.
- Go to the listed paths:
%USERPROFILE%\Desktop
%USERPROFILE%\Downloads
%TEMP% - Locate a file that could be the ransomware’s launcher, right-click it, and choose Delete.
- Find a text file titled CoronaVirus.txt, right-click it, and choose Delete.
- Close File Explorer.
- Empty Recycle Bin.
- Reboot the computer.
Coronavirus Ransomware Screenshots: