CVC Ransomware Removal Guide
It is easy to protect Windows against CVC Ransomware, but it is not that easy to restore normal order and remove the infection once it slithers in. If you have found yourself in a situation where you need to erase this malware, perhaps you can remember opening a strange email attachment recently. Spam emails are often used for the distribution of malware, and cybercriminals only need to put in minimal effort to make the messages intriguing or legitimate-looking. If the message tricks the recipient, they might decide to open a file or link attached to it. This action, unfortunately, can lead to the infiltration of ransomware. Is that what you are dealing with at this time? If it is, we can help you delete CVC Ransomware, but we cannot guarantee that you will be able to restore your personal files in the end. There is a free Rakhni Decryptor that you might be able to use successfully, but it seems that the only guaranteed way of restoring files is by replacing them. Obviously, that is possible only if copies of the corrupted files exist.
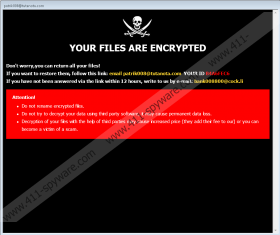
Evidently, CVC Ransomware is a clone of HCK Ransomware, CLUB Ransomware, LCK Ransomware, ROGER Ransomware, and other infections from the Crysis/Dharma Ransomware family. This malware can slither into your operating in all kinds of ways, and because the attackers behind them are generally experienced, they know exactly how to attack you. If CVC Ransomware slithers in successfully, the encryption of your personal files begins shortly after that. The “.id-{unique ID}.[patrik008@tutanota.com].cvc” extension is added to the names of the corrupted files to help you identify them quicker. If you try to open these files, you should discover that they cannot be read normally. That is because the data of your files is changed, and only a decryptor can restore it back to normal. Unfortunately, you cannot employ just any decryptor. It has to match the encryptor, and that means that cybercriminals are the ones who obtain it. Of course, you have the Rakhni Decryptor, but we cannot guarantee that it can restore all files. Does that mean that you should rely on the decryptor proposed by cybercriminals? Absolutely not.
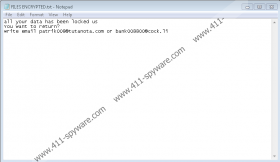
CVC Ransomware drops “Info.hta” and “FILES ENCRYPTED.txt” files on all infected systems. The first file launches the “patrik008@tutanota.com” window, and it displays a message that urges victims to send a unique ID code to patrik008@tutanota.com or bank008800@cock.li. The message also warns that renaming files and employing third-party decryptors would certainly harm your files. That is not the truth. The .TXT file simply suggests emailing the same two addresses if one wants to restore files. So, did the attackers create CVC Ransomware to make you email them? In a sense, they did, but they want you to contact them just so that they could suggest purchasing a decryptor from them. Do you think that you can trust cybercriminals? Of course, you cannot, and so you should be careful about what promises you pay attention to and what instructions you follow. Note that if you email the attackers, they could scam you in the future via your inbox, and if you pay the ransom, you are unlikely to get anything in return.
Unfortunately, your files will remain encrypted after you remove CVC Ransomware, but remove this malware you must. Ideally, once that is taken care of, you can replace the corrupted files with backup copies stored someplace else, or you can employ the free decryptor mentioned above. Of course, you have to figure out how to delete CVC Ransomware first. One option is to do that manually, and the guide below demonstrates how to do it. Note that not all components have concrete names or even concrete locations, and that is why inexperienced users might have trouble eliminating this malware. On the other hand, the removal of this threat is not a big challenge for legitimate anti-malware software. We advise installing it anyway for full Windows protection, and so you might as well use it for the elimination of the ransomware as well.
How to delete CVC Ransomware
- If you can locate the {random name}.exe file that launched the threat, Delete it.
- Locate and Delete all copies of the file named FILES ENCRYPTED.txt.
- Open File Explorer (tap Win+E keys) and enter the following pathsinto the quick access bar:
- %APPDATA%
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\
- %ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup\
- %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup\
- If you can find Info.hta and {unique name}.exe files, Delete them immediately.
- Open Run (tap Win+R keys) and enter regedit into the dialog box.
- In Registry Editor, go to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
- If you can find {unknown name} values linked to Info.hta and {unique name}.exe files, Delete them.
- Exit all opened windows and then Empty Recycle Bin.
- Install a genuine malware scanner and then perform a complete system scan to check for leftovers.
CVC Ransomware Screenshots: