EG83 Ransomware Removal Guide
Can you protect your Windows operating system against EG83 Ransomware? That depends on what security measures you have taken to protect it against malware, whether RDP connection is enabled, and whether you have file-sharing enabled. Unprotected systems with this feature enabled can become targets of an attack conducted by the attackers behind the Matrix Ransomware family. The way this malware works is that it tries to infect all systems that are reachable via file-sharing and RDP. That means that if you are unable to protect yourself against malware, you could be responsible for the suffering of others too. How can you delete EG83 Ransomware once it slithers in? In fact, you might not need to worry about this because, according to our team, the attackers are likely to remove it for you. Nonetheless, the damage left behind could be enough to cause a headache.
BDDY Ransomware, Matrix-THDA Ransomware, and Matrix-EMAN Ransomware are all clones of EG83 Ransomware. They all attack systems using unsecure RDP connections, and they all encrypt personal files. The attack is quick, and you might not notice when your personal files become unreadable. However, once the attack is complete, you cannot miss which files were corrupted because their names are changed completely. Not only are original names scrambled, an additional extension and prefix are added too. This makes all of your personal files look like this: “[Evagreps83@yahoo.com].{random characters instead of original name}.EG83.” Is there something you can do to read and decrypt your files? Form our standpoint, there isn’t. A legitimate decryptor that would be able to decipher this malware does not exist (not at the time of research, at least), and decrypting files manually is not possible. However, the criminals behind EG83 Ransomware want you to think that you can do something.
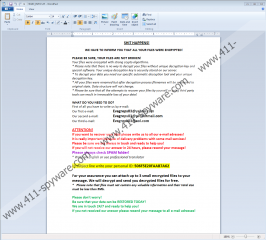
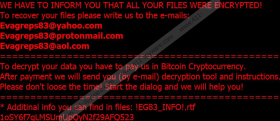
Have you noticed that the wallpaper of your background has changed? EG83 Ransomware changes it with a file dropped to %APPDATA%. According to the message that is represented via the image file, your files were encrypted, and now you must email Evagreps83@yahoo.com, Evagreps83@protonmail.com, and/or Evagreps83@aol.com. The message also informs that you “have to pay in Bitcoin Cryptocurrency” to obtain a decryption tool that, supposedly, would free your files. EG83 Ransomware also drops a file named “!EG83_INFO!.rtf” in every folder that contains encrypted files. The message represented via this file does not say anything about a ransom payment, but it alleges that files can be decrypted only if a special tool and key are used. So, what does a victim of this ransomware do after reading such proclamations? Some of them are likely to send an email and then pay a ransom. We believe that that is a mistake. First of all, you never know what the attackers could send via email in the future. Second, how can you be sure that a decryptor would be presented in return for your money? We doubt that it would.
Some Windows users set up restore points to ensure that they can always go back in time, so to speak, to salvage any data that they might lose or delete accidentally. Unfortunately, EG83 Ransomware deletes shadow volume copies, and so this is no longer an option. What about backups? If you use online or external backups to store copies of personal files, you can use them as replacements, but you must remove EG83 Ransomware first. As we mentioned already, this threat is likely to be eliminated by the time you discover it, but when it comes to malware, we suggest erring on the side of caution. We strongly recommend installing anti-malware software that could inspect your system for leftovers and also perform automated removal if necessary. Another great thing about this software is that it can ensure protection afterward. Besides taking care of security – which is the number-one priority – you also need to secure your RDP connections and reassess file-sharing. If your system was infected, and you have other computers connected via file-sharing, warn their users about a potential ransomware attack.
How to delete EG83 Ransomware
- Delete all versions of the !EG83_INFO!.rtf file.
- Open File Explorer by tapping Win+E keys and enter %APPDATA% into quick access.
- Delete the {random name}.bmp file and then set the desired wallpaper.
- Delete any recently downloaded files that you might identify as malicious files.
- Once you think you are done, Empty Recycle Bin.
- Immediately employ a trusted malware scanner to help you with a full system scan.
EG83 Ransomware Screenshots: