Eight Ransomware Removal Guide
Eight Ransomware is one of those vicious threats that lock files after infecting a system. While it should leave your program data alone, the malware might encipher all your personal files, such as your photos, videos, and data alike. You can recognize the malware from the extension that it appends to all encrypted files; it should look like this: .id[2A2E028A-2796].[use_harrd@protonmail.com].eight. If you see an extension that except the ID number looks the same on your files, we invite you to read our full report to learn about the threat that you most likely came across. In the article, we explain how it works, what could you do, and why it is best to erase Eight Ransomware. Also, we display deletion instructions just a bit below the text.
To start with, we should tell you how Eight Ransomware might be spread. Usually, such malicious programs are distributed via spam emails, harmful file-sharing websites, or unsecured RDP (Remote Desktop Protocol) connections. Consequently, we recommend doing three things to protect your computer from ransomware. First, you should never open attachments or files sent via any kids of messages if you are not certain that they are safe or if they raise suspicion. Second, you should never download updates, software installers, and data alike from torrent or other file-sharing sites as data offered there could be infected with various threats. Our third advise is to secure your RDP connections and disable them whenever you do not need them. Plus, whenever you are in doubt, you should scan files in question with a reliable antimalware tool. It can help you learn instantly whether a file is malicious or not.
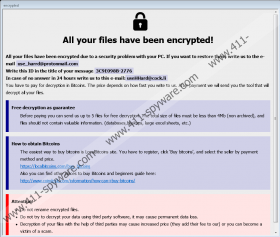
If the Eight Ransomware’s installer gets launched, the malware should create a few copies of its launcher in different locations. Also, the malicious application might create a couple of Registry entries that would make an infected device open it automatically after every restart. In other words, the malware might auto start with your system as long as you let it stay on your computer. After its launch it should locate the files that it was programmed to encipher. As mentioned earlier, Eight Ransomware should be after pictures, various documents, and other files that do not belong to the computer’s operating system or other programs. Since targeted data gets encrypted with a robust encryption algorithm, it cannot be decrypted unless a user has a unique decryption key and a decryptor. The note that ought to be created after the encryption process, should say that hackers have such means and are willing to provide victims with them if they pay ransom.
Naturally, if you have money to spare, paying a ransom could be one of the ways to get your files back. The problem is that you cannot know if the malware’s developers will keep up with their promise. Meaning, paying a ransom would be dangerous as you could lose your money in vain. The other option is to erase encrypted files and get your backup data to replace them. Needless to say that this can only work if you created a backup on cloud storage, a removable media device, or elsewhere before your files got encrypted. Of course, to ensure that your backup files or any new data that you might create or download in the future would not get encrypted too, you should delete Eight Ransomware.
While it is possible to remove Eight Ransomware manually, the task could be challenging. Still, if you want to try, you could use the instructions located below this paragraph. On the other hand, if you find the process too tricky, we advise getting a reliable antimalware tool that would erase Eight Ransomware for you.
Get rid of Eight Ransomware
- Press Ctrl+Alt+Delete.
- Select Task Manager.
- Go to the Processes tab.
- Search for a process belonging to the malware, select it, and press End Task.
- Exit Task Manager.
- Press Win+E.
- Check your Desktop, Temporary Files, and Downloads directories.
- Find the malicious file that infected your computer, right-click this file, and click Delete.
- Navigate to these directories:
%LOCALAPPDATA%
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup
%ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup - Look for malicious .exe files belonging to the infection, right-click them, and select Delete.
- Go to these directories:
%USERPROFILE%\Desktop
%HOMEDRIVE% - Find files called Info.hta, right-click them, and select Delete.
- Close File Explorer.
- Click Win+R.
- Type regedit and click Enter.
- Check these paths:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run - Look for value names with value data that points to: C:\Users\User\AppData\Local\{random}.exe
- Right-click malicious value names and press Delete.
- Exit Registry Editor.
- Empty Recycle Bin.
- Reboot your system.
Eight Ransomware Screenshots: