Geno Ransomware Removal Guide
Photos and documents cannot be safe with Geno Ransomware around, and that is why you must do everything to ensure that this malware cannot penetrate the security walls surrounding your operating system. It is most important to make sure that all security updates are installed to ensure that the implemented security tools are able to guard the system appropriately. What about keeping the system guarded against malicious invaders without the help of anti-malware software? In theory, that is possible. In practice, that is very hard to ensure. Therefore, if you still have time to keep malware away, we recommend that you implement some kind of security tool as soon as possible. If your system was hit already, your first priority should be removing malware, but securing the system is just as important. Luckily, you can both delete Geno Ransomware and secure your system all at once.
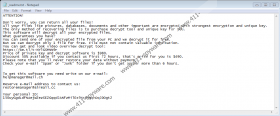
Our research team informs that Geno Ransomware is a clone of Usam Ransomware, Odgo Ransomware, Moba Ransomware, and hundreds of other threats that are meant to encrypt personal files on Windows systems. In some cases, we see malware that is built and sold for willing parties, but these clones appear to be controlled by one attacker. All variants fall under the umbrella name ‘STOP Ransomware,’ and they all use a file named “_readme.txt” to deliver one message. It is always the same, and it is meant to make victims think that they can retrieve a decryptor by contacting the attackers and paying a ransom. You are supposed to send a message to helpmanager@mail.ch or restoremanager@airmail.cc. Because we have reviewed the most active clones of Geno Ransomware, we know that these email addresses have been pinned to the ransom note file that most of them display. The only distinction between these clones is the extension that is added to the corrupted files, and “.geno” is the extension that is linked to the Geno variant. Do not bother deleting this extension because that will not help with anything.
So, what do the attackers behind Geno Ransomware want? They want your money, and they suggest that as soon as you pay a ransom of $490, they will give you a decryptor that, allegedly, will restore all files. Can you trust them? We do not believe that cybercriminals can be trusted, and so we do not recommend that you send emails, try to come up with deals, or succumb to any ransom demands. In the worst-case scenario, by taking these risky moves, you will expose yourself to new scams via email, and your money will go to waste. Of course, if the encrypted files matter, you might see no other option but to obey. Well, what about a free decryptor? STOP Decryptor is a tool that is meant to work for the victims of STOP Ransomware. It cannot decrypt all files, but it might offer relief for some. Another option is to recover files from backup. If you have stored copies of the encrypted files outside the infected computer, you can use these copies as replacements, but note that you can do that only after you remove Geno Ransomware.
What kind of experience do you have with the removal of malware? If it is limited or non-existent, removing Geno Ransomware manually might be too challenging and even dangerous. After all, you do not want to create more problems, do you? If you are sure that you can handle the threat yourself, we hope that the steps below can help you. The second option to consider is implementing anti-malware software. As we talked before, the existence of this software is imperative if you want to keep your operating system safe and malware-free. If you employ it now, it will help you avoid malware in the future, and at the same time, it will also remove Geno Ransomware and any other malware, should it exist. Of course, you must not rely on security tools alone. In the future, beware of spam emails, downloaders, pop-ups, fake updates, and RDP vulnerabilities that could be exploited for the execution of dangerous malware.
How to delete Geno Ransomware
- Tap Windows+E keys to launch File Explorer.
- Enter %HOMEDRIVE% at the top to access the directory.
- Delete a file named _readme.txt.
- Delete a folder named SystemID.
- Enter %LOCALAPPDATA% at the top.
- Delete a folder with name like 0115174b-bd55-4caf-a89a-d8ff8132151f.
- Empty Recycle Bin once you think you are done.
- Use a legitimate malware scanner to scan your system for leftovers.
Geno Ransomware Screenshots: