GTF Ransomware Removal Guide
Did you open a strange email attachment or downloaded a new file from an unfamiliar source before the malicious GTF Ransomware attacked? If you remember taking an action like that, it seems that you yourself are responsible for the invasion of this malware. The same methods of attack are employed by all other infections from the Crysis/Dharma Ransomware family, including Rxx Ransomware, 8800 Ransomware, or Devil Ransomware. These malicious infections can stay under the radar until it is time to reveal themselves, and victims might be unable to identify this malware when it attacks. This is why the protection provided by legitimate anti-malware software is so important. This software does not care about what kind of a disguise an infection might employ. As long as it can identify malware files, it should be able to remove them instantly. If the infection got in already, you are responsible for getting it out. So, do you know how to delete GTF Ransomware?
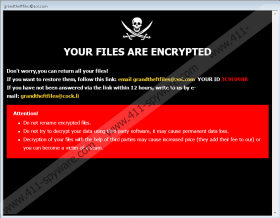
Since you are not supposed to realize when GTF Ransomware slithers in, you should be surprised when you discover that your personal files cannot be read and that they have an additional extension (“.id-{unique ID}.[grandtheftfiles@aol.com].GTF”) appended to their names. Before that, you might face a window named “grandtheftfiles@aol.com.” The ransomware drops a file called “Info.hta,” and this is the file that is responsible for the window. The message represented via it reads: “YOUR FILES ARE ENCRYPTED Don't worry, you can return all your files! If you want to restore them, follow this link.” The message then lists two email addresses (grandtheftfiles@aol.com or grandtheftfiles@cock.li) that you are meant to send messages to if you want to have all personal files decrypted. Is it safe to contact the attackers? It is not, and if you are sure that you want to send a message to learn exactly what the attackers want, you should at least create a separate email account that you could, later on, delete. If you use your own email account, you could have it flooded with misleading messages, sextortion scams, and spam.
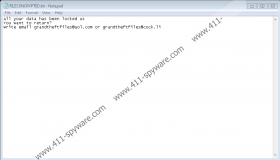
Another file that GTF Ransomware drops is called “FILES ENCRYPTED.txt.” It also lists the same two email addresses, and it simply states that data can be “returned” only if the victim contacts the attackers. Well, if you contact them, they will send you ransom payment instructions. If you pay the ransom, you will get nothing in return. In theory, the attackers could provide you with a decryptor. In practice, they do not need to and so they are unlikely to do it. If you do not mind wasting money or exposing yourself to cybercriminals, you a free to take whatever risk you want to take. However, we advise that you at least try to get your files back in other ways first. For example, think about what backups/copies you already have. If you have copies of the most important files, you should be able to replace them after removing GTF Ransomware. What about free decryptors? Crysis/Dharma decryptors might exist, and you can look into employing them, but please be careful so as not to install anything malicious.
Your Windows operating system is vulnerable. There is no question about that. If you are not going to secure it properly, new infections could attack it in the near future. This is why we advise installing anti-malware software. Use it to protect your system and also automatically remove GTF Ransomware. If you are thinking about taking the manual removal route, we have a guide for you, but note that you need to identify the launcher yourself, because we do not know what its name could be. Afterward, use copies to replace files or a decryptor to restore the corrupted files. In the future, always remember to create copies and store them on external or virtual drives to ensure that you have a plan B in case something goes awry again. Note that there are thousands upon thousands of infections that can corrupt or even delete your personal files. Also, you cannot predict hard drive damage or loss of devices.
How to delete GTF Ransomware
- If you can identify the {unknown name}.exe launcher file, right-click and Delete it.
- Right-click and Delete the FLES ENCRYPTED.txt file.
- Launch File Explorer (tap Win+E keys) and enter the following pathsinto the field at the top:
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\
- %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup\
- %ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup\
- %WINDIR%\System32\
- %APPDATA%
- Right-click and Delete the file named Info.hta and also {unknown name}.exe file.
- Launch Run (tap Win+R keys) and enter regedit into the dialog box to access Registry Editor.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
- Right-click and Delete all values with random names that are set up by ransomware.
- Empty Recycle Bin and quickly employ a legitimate malware scanner to scan your system for malware.
GTF Ransomware Screenshots: