HDD Encrypt Ransomware Removal Guide
We want to inform you about a newly discovered ransomware that cyber security specialists have dubbed HDD Encrypt Ransomware. You must remove this application if it happens to infect your computer because it is configured to scan it for files to encrypt them using an advanced encryption algorithm. After encrypting them, this ransomware will offer you to contact the developers of the decryption key, but keep in mind that you will not get it for free. Make no mistake, this program was created with the intention of extracting money from users that have been unfortunate to have their computers infected with this ransomware. For more information, please read this whole article.
Not much is known about this ransomware's origins or how it is distributed, but we will provide you with information on the most likely distributed method implemented by its developers because that is how most ransomware is distributed these days. We believe that HDD Encrypt Ransomware is sent to unwary users around the globe in malicious emails that contain zipped attachments that drop this ransomware's main executable when opened. The emails are most likely tailored to look like they have been sent from legitimate companies such as DHL, FedEx, Amazon, and so on, and the zipped file may be named “invoice,” “receipt” or something of that nature, giving the impression that it is a document you need to open. Furthermore, the text inside the email is likely to point you to the file and use subtle persuasion tactics to encourage you to open the email.
If you open the zipped file, then HDD Encrypt Ransomware’s executable will be dropped in %HOMEDRIVE%\C22. The executable does not have a preset name, so its name is generated randomly with uppercase and lowercase characters and other symbols. The executable is set to run automatically, and once it does, it will scan your computer for files of interest, but it will not cherry-pick them. Testing has shown that it will encrypt files such as, .xls, .ppt, .jpg, .exe, .png, .dll, .odt, .csv, .sql,, .mdb, .hwp, .pdf, .bin, .db, .dat, .mkv, .mml, .mov, .mp3, .mp4, and many other file types. We have yet to determine what kind of encryption method this ransomware is set to use, but we are positive that it will be either the AES or RSA encryption systems because they are the most commonly used by ransomware developers.
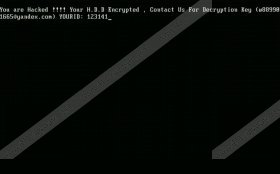
Unlike most ransomware-type infections that drop a ransom note text file after encrypting the files, HDD Encrypt Ransomware overwrites MBR (Master Boot Record) and restarts the computer automatically. As a result, the computer will not boot, and you will be presented with a screen with text that reads "You are hacked !!! Your H.D.D. Encrypted , Contact US For Decryption KEY (w889901665@yandex.com) YOURID: {6 digit ID number}.” So you will not be able to use the same computer to contact the cyber criminals. We have no doubt that they will demand that you pay money in Bitcoins for the decryption key which you might not even get after paying. Therefore, you should refrain from complying with their demands and seek for ways to get back control of your computer.
While running our tests, we tried to repair the MBR by running the repair program found on the Windows installation DVD/CD. This should work for Windows XP and later once you have fixed the MBR and your computer is able to boot Windows, you can proceed to remove HDD Encrypt Ransomware. You can either delete its executable manually or opt for an anti-malware program such as SpyHunter that will make light work of this ransomware.
Fix the Master Boot Record (MBR)
Windows XP
- Insert the CD of Windows XP in the CD/DVD-ROM.
- While restarting the PC, press any key to boot.
- Press the R key to open the Recovery Console.
- Type 1 and press Enter if Windows XP is your only OS.
- Enter your administrator password and hit Enter.
- Press the Y key and then hit Enter.
- Eject the CD from the CD/DVD-ROM.
- Type Exit and then press Enter to restart your PC.
Windows Vista
- Insert the CD of Windows Vista in the CD/DVD-ROM.
- While restarting the PC, press any key to boot.
- Select the language and keyboard layout.
- Click Repair your computer.
- Select the operating system.
- Click Next.
- Open Command Prompt.
- Type the following commands.
- bootrec /FixMbr and press Enter.
- bootrec /FixBoot and press Enter.
- bootrec /RebuildBcd and press Enter.
- Remove your CD and type exit.
- Press Enter.
Windows 7
- Insert the DVD of Windows 7 in the CD/DVD-ROM.
- While restarting the PC, press any key to boot.
- Select your language and keyboard layout.
- Click Next.
- Select the OS.
- Click Next.
- Click Command Promptto open it.
- Type bootrec /rebuildbcd and press Enter.
- Type bootrec /fixmbr and press Enter.
- Type bootrec /fixboot press Enter.
- Remove the DVD and restart your computer.
Windows 8/8.1/10
- Insert the DVD of Windows 7 in the CD/DVD-ROM.
- While restarting the PC, press any key to boot.
- Click Repair your computer at the Welcome screen.
- Click Troubleshoot and open Command Prompt.
- Type bootrec /FixMbr and hit Enter.
- Type bootrec /FixBoot and hit Enter.
- Type bootrec /ScanOs and hit Enter.
- Type bootrec /RebuildBcd and hit Enter.
- Remove the DVD from the CD/DVD-ROM.
- Type Exit and then press Enter.
- Reboot your computer.
Delete HDD Encrypt Ransomware
- Hold down Windows+E keys.
- In File Explorer’s address line, enter %HOMEDRIVE%
- Right-click the C22 folder and click Delete.
- Empty the Recycle Bin.
- Done.
HDD Encrypt Ransomware Screenshots: