Hets Ransomware Removal Guide
Hets Ransomware is a variant of STOP Ransomware, and like most of them, it encrypts data and shows a note asking to pay 490 US dollars in 72 hours or 980 US dollars if a user needs more time to pay. In exchange, the malware’s creators promise to provide decryption software. You might not want to lose a chance to spend less, but we advise not to rush. First, it is crucial to realize that no matter what the hackers may promise, there are no reassurances that they will do it. Meaning, they may not bother sending you the guaranteed decryption software. Also, it would be smarter to see if you can restore any files on your own, for example, by replacing them with backup copies. Naturally, if you do not need decryption software to get your data back or you do not want to fund cybercriminals and risk your money, we advise deleting Hets Ransomware. To learn more about it, you should read the rest of this article.
Hets Ransomware could be received via unreliable emails and other types of messages or downloaded from untrustworthy file-sharing sites. Therefore, we highly recommend not to open any data that comes from questionable sources. If you want to protect your system from malware, you have to be one hundred percent sure that the files you receive or download are harmless. If you do not know, we recommend scanning suspicious files with a chosen antimalware tool first. If you do not have a security tool yet, you should pick a legitimate tool that comes from a reputable company and can detect various types of malicious applications.
According to our specialists, Hets Ransomware should settle in by creating a randomly named folder in the %LOCALAPPDATA% and other data that is mentioned in our removal instructions. Afterward, it should start encrypting files that are not related to the computer’s operating system or other programs installed on it. It means that the malicious application should encipher pictures, photos, documents, and other files that could be personal and irreplaceable. Every file that gets encrypted should get a second extension called .hets. For instance, a text document named introduction.docx would become introduction.docx.hets after being encrypted by Hets Ransomware. Once the malware encrypts all the files that it is after, it should drop a ransom note called _readme.txt.
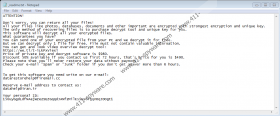
Inside of _readme.txt, you should see an explanation of why you can no longer access files that have the .hets extension as well as instructions on what to do to decrypt them. To be more specific, Hets Ransomware’s note should ask to contact the threat’s developers and pay a ransom. To ensure victims that the hackers have the needed decryption software, they offer decrypting a single file of no importance free of charge. Remember that encrypting a file does not prove that you will get the needed decryption software. Once the money reaches the Hets Ransomware’s developers, they could do anything they want with it, whether they deliver decryption software or not. Therefore, the money you pay would be lost for nothing, and you would still have no means to get your files back.
As mentioned earlier, your files could be replaced with backup copies. Also, sometimes cybersecurity experts create free decryption software for victims of such threats, which is why it might be a good idea to check for such tools from time to time if you have no way to get your data back. Finally, no matter what you decide to do about the hackers’ proposal, we advise deleting Hets Ransomware. Leaving it on your system could endanger your future data. Thus, if you do not want to put your files at risk, we recommend removing Hets Ransomware while following the instructions located below or with a reliable antimalware tool.
Get rid of Hets Ransomware
- Tap Ctrl+Alt+Delete.
- Pick Task Manager.
- Select the Processes tab.
- Look for a process associated with the malware.
- Select the process and click End Task.
- Leave Task Manager.
- Tap Win+E.
- Go to these locations:
%TEMP%
%USERPROFILE%\Downloads
%USERPROFILE%\Desktop - Find the malicious file opened before the system got infected, right-click it, and select Delete.
- Search for files named _readme.txt and PersonalID.txt, right-click them, and select Delete.
- Check this location: %LOCALAPPDATA%
- See if you can find the malware’s folder with a random name, e.g., 0215171b-ba55-7xal-a49s-c2fk4162159c, right-click it, and choose Delete.
- Close File Explorer.
- Empty Recycle Bin.
- Restart the computer.
Hets Ransomware Screenshots: