Howareyou Ransomware Removal Guide
No one wants to experience a ransomware infection, but sometimes things like Howareyou Ransomware manage to enter our systems, and then we have to battle these threats. The prospects of this infection are rather bleak because it is not a high-profile program. It means that there is no public decryption tool available, and users have to look for ways to restore their files themselves. However, we hope that you will remove Howareyou Ransomware from your system as soon as possible because there is no need to listen to what this infection has to say.
As far as our research team has found, this infection doesn’t differ much from all the other ransomware programs that we have discussed before. To put you in a dire situation, Howareyou Ransomware encrypts all your picture and document files. Usually, ransomware infections target files that are stored in the %USERPROFILE% directory. It is the default user storage directory with the main Videos, Pictures, Documents, and other folders that we’re all used to. Hence, if you keep important files there, you can be sure that in the case of a ransomware infection, those files will be locked up.
When the infection is launched, Howareyou Ransomware encrypts all targeted files and appends a new extension. Most of the time, ransomware infection names come exactly from those extensions. Hence, it shouldn’t come as a surprise that the appended extension for this infection is “.howareyou.” This line will be added to all the files that were affected by the encryption. In a way, it functions like a stamp that shows you which files were tampered with. But other than that, it doesn’t give you any kind of upper hand, aside from knowing that you were infected with Howareyou Ransomware.
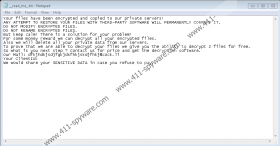
Every single folder that contains encrypted files also gets a ransom note file _read_me_.txt. If you open that file, you can find the following ransom note:
Your files have been encrypted and copied to our private servers!
ANY ATTEMPT TO RESTORE YOUR FILES WITH THIRD-PARTY SOFTWARE WILL PERMANENTLY CORRUPT IT.
DO NOT MODIFY ENCRYPTED FILES.
DO NOT RENAME ENCRYPTED FILES.
<…>
For some money reward we can decrypt all your encrypted files.
Also we will delete all your private data from our servers.
The note goes on to say that you can contact these criminals via the given email address. It doesn’t say exactly how much you are expected to pay for the decryption key, but you can be sure that the amount will be staggering. So, should you ever follow these crazy instructions? Of course, you shouldn’t.
However, the problem with ransomware is that prevention is even more important that the actual “medicine.” Let’s say that prevention is like a vaccine that allows you to avoid this terrible virus. How can you be vaccinated? By learning more about ransomware distribution methods, of course! Ransomware usually travels via spam email attachments, and if you learn to differentiate between regular emails and fake scam emails, you will surely avoid the likes of Howareyou Ransomware, too.
To learn more about ransomware distribution and other preemptive measures that would help you avoid such intruders, please do not hesitate to leave us a comment below. We believe that every case should have an individual approach.
Also, you can use the manual removal instructions below to remove Howareyou Ransomware from your computer. It is also strongly recommended to employ a powerful antispyware tool that would safeguard your system against all sorts of threats. Finally, please consider addressing a local professional to find out more about all the possible file recovery options. Don’t let these crooks win.
How to Delete Howareyou Ransomware
- Delete the most recent files from Desktop.
- Remove the latest files from the Downloads folder.
- Press Win+R and enter %TEMP%. Click OK.
- Remove the most recent files from the directory.
- Perform a full system scan with SpyHunter.
Howareyou Ransomware Screenshots: