JesusCrypt Ransomware Removal Guide
When JesusCrypt Ransomware encrypts files, the “.jc” extension gets appended, and this extension is the marker that you can use to quickly determine which files were encrypted and which ones were spared. When we first came across this malicious threat, it was not fully developed yet, and so it is no surprise that no one has created a decryptor to match it. Unfortunately, we cannot guarantee that a decryptor will be created because, as you might know already, most file-encrypting infections remain undecryptable. That is because cybercriminals use unique encryption algorithms, and it is not so easy to crack them. The threat was built using the Hidden Tear code, which is the same code that was used by TrumpHead Ransomware, SnowPicnic Ransomware, ShutUpAndDance Ransomware, and many other infections. Free tools called “HiddenTear Decryptor” and “HiddenTearDecrypter” exist, but we cannot guarantee that you will be able to use them to free your files. Unfortunately, files cannot be freed by deleting JesusCrypt Ransomware either, and so victims of this malware might choose to follow their attackers’ demands. That is a mistake.
You might not know how JesusCrypt Ransomware slithered in, or you might be able to pinpoint the exact moment it got in. That depends on how this malware is introduced to you. If your files are encrypted soon after you download a new program or open a strange email attachment, it should be obvious how the threat got in. However, JesusCrypt Ransomware could also be downloaded and executed by other infections (if they exist, they must be removed!), or cybercriminals could exploit vulnerabilities within the system and the installed software. All in all, if you do not notice the infection when it slithers in, you cannot remove it in time, and if you do not remove it, your personal files are encrypted right away. The threat can encrypt ".jpg", ".jpeg", ".raw", ".tif", ".gif", ".png", ".bmp", and many other types of files, and once they are encrypted – they cannot be read. That is due to the changes within the data of these files. Besides corrupting files, it appears that the malicious infection is also capable of messing with every program that opens a window. Whether it is the Task Manager, the Command Prompt, or the browser, the threat might be able to kill the process and prevent you from using the program.
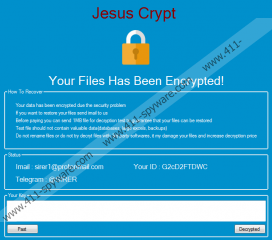
Once files are encrypted and the control of your operating system is taken over, JesusCrypt Ransomware launches a window. It represents the name of the threat and a message, using which cybercriminals can try to convince you to send them a message. If you send a message to sirer1@protonmail.com, the attackers will immediately respond with instructions on how to pay the ransom. According to the message that is represented using the “READ_IT.txt” file on the Desktop, the ransom is $200, and you must pay it in Bitcoin. Do you have that kind of money? Do you want to pay the ransom? Are you ready to expose yourself to cybercriminals via email? You might think that you are already exposed if the threat was introduced to you via email, but the launcher is sent to thousands of users randomly, and cybercriminals do not really know whether or not the account is active unless you respond back. We do not want you facing new threats and scams, and we also do not want you losing money, which is why we do not recommend communicating with the attackers behind JesusCrypt Ransomware.
Since JesusCrypt Ransomware is still in development, we cannot know exactly how it will turn out. That being said, we do not want to wait to see, and it is better to warn you about this threat now, before it starts invading Windows systems actively. Of course, we hope that that will never happen. If the infection is unleashed, we hope that you can prevent it from killing processes by restarting your computer. If that does not help, you might need to reboot into Safe Mode to remove JesusCrypt Ransomware launcher or into Safe Mode with Networking to install a reliable anti-malware tool that will be able to detect and delete the infection automatically. Should you pay the ransom before removing the infection? Since you are unlikely to obtain a decryptor by doing that, we do not recommend it. In the future, if you want to avoid malware, always backup your files (if you have backups, you can replace the locked files), install updates, and stay away from strange emails, downloaders/installers, pop-ups, suggestions, etc.
How to delete JesusCrypt Ransomware
- Move to the Desktop and Delete the file named READ_IT.txt.
- Identify the malicious launcher file (unknown location/name) and Delete it.
- To complete the removal, Empty Recycle Bin.
- Install a malware scanner you can trust.
- Perform a full system scan and use it to check for malicious leftovers.
JesusCrypt Ransomware Screenshots: