Jope Ransomware Removal Guide
Jope Ransomware attacks Windows operating systems, and it does that silently. Spam emails, social engineering scams, RDP vulnerabilities, clandestine downloaders, and even silent trojans could be used to expose Windows users to the infection’s launcher. If the target’s system has a good security system, the launcher file should be recognized and removed instantly. If a security system does not exist or is weak, the launcher executes and immediately gets on with the encryption of private files. This malware does not care about system files, but it cares very much about your photos, documents, and other files alike. Once they are encrypted, you should find the “.jope” extension appended to them, which indicates that files cannot be read. Unfortunately, if your files get encrypted successfully, the attackers behind the infection might have a chance at tricking you into giving up a huge sum of money. Of course, whether or not you get roped into the scam, you must delete Jope Ransomware.
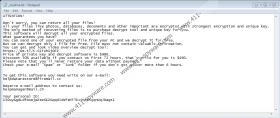
STOP Ransomware is the predecessor of Jope Ransomware as well as Mpaj Ransomware, Ooss Ransomware, and hundreds of other file-encrypting threats. These infections all look, spread, and function in the same way, and that is because cybercriminals have found the winning formula. Why would they change anything when the threat works? After infiltration, files are encrypted, and then Jope Ransomware immediately drops a file named “_readme.txt.” The message inside the file informs that victims can recover their files only if they agree to pay a ransom of $490. That is not the only condition. Victims also are required to send an email to helpdatarestore@firemail.cc or helpmanager@mail.ch. Needless to say, if you contact cybercriminals, they could try to scam you, and that could cause more problems for you. Let’s say the attackers leak your email address online, where all other schemers and cybercriminals can find it. The next thing you know, your inbox is flooding with spam emails, fake messages about lottery winnings, ads for undesirable products or services, as well as terrorizing messages claiming that someone has compromising videos or images of you. The possibilities are endless.
If you contact the attackers behind Jope Ransomware and then pay the ransom, many different things could happen, but one thing that is unlikely to happen is that you would get the decryptor. The attackers only promise to give it to you so that you would send them your money. After you do that, your money cannot be returned to you. There are thousands of file-encrypting threats in the virtual world, and most of them are undecryptable, which means that most victims are unable to salvage their files, unless backup copies exist somewhere safe. That is not necessarily the case with Jope Ransomware. According to our research team, a tool called STOP Decryptor was built by security researchers, and it can be downloaded for free by anyone. The tool is meant to decipher the STOP Ransomware encryption keys used to lock files, but of course, because new variants emerge almost daily, some victims might have to wait. Unfortunately, only files encrypted with an offline key can be salvaged as well. Basically, STOP Decryptor does not guarantee anything. This is why we hope that you have replacement copies.
Can you replace the files that were corrupted by Jope Ransomware? If you can, you should do that only after you remove the infection. How should you do it? You have several options to choose from. You can install a legitimate anti-malware tool, which is built to detect and delete malware components from Windows automatically. Alternatively, you can try to find and remove Jope Ransomware files yourself. The guide below gives you the basic idea of what needs to be erased, but if you cannot find the launcher, you are unlikely to succeed on your own. All in all, you have to secure your Windows system to prevent malware invasion in the future, and so it is prefect time to install anti-malware software. It will simultaneously erase active threats and secure your system against all others.
How to delete Jope Ransomware
- If you can identify the launcher of the infection, Delete it.
- Simultaneously tap Windows+E keys for File Explorer.
- Enter %LOCALAPPDATA% into the field at the top.
- Delete a folder with a random name that was created by Jope.
- Enter %HOMEDRIVE% into the field at the top.
- Delete the ransom note file, _readme.txt.
- Also, Delete the folder named SystemID.
- Exit File Explorer and then Empty Recycle Bin.
- Install a legitimate malware scanner and scan the system for leftovers.
Jope Ransomware Screenshots: