Lisp Ransomware Removal Guide
If you want to protect your system against threats like Lisp Ransomware, you need to build a fortress around it. It might seem like a complicated, time-consuming task, but it is not. The main element is reliable security software that could guard your operating system against attackers, invaders, and malware distributors. To strengthen the walls of the fortress, you also need to act as a watchman. Watch out for unreliable downloaders introduced via file-sharing websites as well as pop-ups and ads that might introduce you to alleged updates for your system or the installed software. Furthermore, watch your inbox closely. Remove all emails from the spam folder, and assess messages that land in your main inbox to ensure that that you never open emails sent by schemers and cybercriminals. You might need to work on this in the future, after you delete Lisp Ransomware from your system. Unfortunately, if this threat got in, it is possible that your personal files were lost.
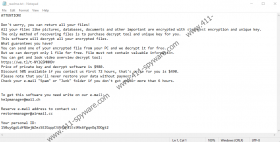
Lisp Ransomware might also be identified as STOP Ransomware because this is the infection that the new malware has been modeled after. In fact, hundreds of identical threats have been modeled after it, including Epor Ransomware, Foqe Ransomware, Mmpa Ransomware, Efji Ransomware, and so on. For the most part, these infections have four-letter names that make no sense. The truth is that these names are appended to the threats due to the extensions they add to the corrupted files. Lisp Ransomware and its clones are set up to encrypt documents, pictures, videos, archives, presentations, and other personal files, and once that is done, the “.lisp” extension is added to their names. For example, after encryption, a file named “meetingschedule.xls” is renamed to “meetingschedule.xls.lisp.” If that was all that the threat did, we would all be very confused. However, it drops a file named “_readme.txt,” and this file delivers a message that was created by the attackers behind the threat.
The attackers want you to believe that all files can be restored, and while it is true that decryptors should exist if encryptors do, we have lots of experience with ransomware, and we can promise you that their creators are generally not interested in decrypting files. In fact, if they share decryptors, in some cases, they can be used by different victims, making future attacks unsuccessful. Therefore, it is only in the interest of cybercriminals to keep their decryptors to themselves. However, that does not mean that they cannot promise decryptors to their victims. The Lisp Ransomware ransom note suggests that you can purchase a decryptor for $490, and who can guarantee that you would get a decryptor in exchange after paying the ransom? No one. Also, you cannot pay the ransom right away. First, you have to email the attackers at helpmanager@mail.ch or restoremanager@airmail.cc, and that is extremely risky to do. It is notable that these email addresses have been represented via the ransom notes of all mentioned Lisp Ransomware clones, which means that they were created by the same attacker(s).
It is crucial to remove Lisp Ransomware and secure your system, but this might fall onto the back burner for now if you are trying to restore your files. Well, you are unlikely to get a decryptor from your attackers, and so we do not recommend following the instructions introduced via the ransom note. However, you could try using the free STOP Decryptor. Will it restore all files? We cannot know that, but this is the only decryptor that existed at the time of research. Of course, you do not need to bother with that if you have copies of your files and can use them as replacements. Needless to say, you should replace files after you delete Lisp Ransomware. In the future, always make sure that your personal files’ copies are stored online or on external drives and devices for safe keeping. Also, do not forget to implement reliable anti-malware software because you need it to turn into a secure fortress.
How to delete Lisp Ransomware
- Open the File Explorer (tap Win+E keys) and enter %LOCALAPPDATA% into the field at the top.
- If you can find a {random name} with a malicious {random name}.exe file inside, Delete it.
- Enter %HOMEDRIVE% into the field at the top of the File Explorer.
- Delete the file named _readme.txt.
- Delete the folder named SystemID if it contains a file named PersonalID.txt inside.
- Exit File Explorer and then Empty Recycle Bin.
- Install a genuine malware scanner to help you examine the system for malware leftovers.
Lisp Ransomware Screenshots: