Locky Ransomware Removal Guide
Locky Ransomware is an infection that people usually download on their computers themselves. We cannot blame them for that because the executable file of this threat is downloaded to the %Temp% folder immediately after users open an infectious email attachment that is usually seen in a form of a Microsoft Word Document. Unfortunately, the email letter itself is usually called Invoice (e.g. ATTN: Invoice J97112346) in order to make sure that a user opens it. If you have already opened the attachment and enabled macros when asked, there is no doubt that Locky Ransomware is installed on your computer. Of course, you will definitely understand that this has happened yourself because all your files will be encrypted, and it will be impossible to open any of them. Unfortunately, this ransomware infection uses the AES encryption, which is considered to be a really strong cipher, so you should not expect that your files will be unlocked after you remove Locky Ransomware from your system completely. Of course, it is still very important to do that because this threat might encrypt other files. In other words, all your new files will be locked again if you do not get rid of ransomware.
As you already know, Locky Ransomware will immediately lock files after it slithers onto the computer. It has been noticed that it will add the {unique_id}{identifier}.locky extension to each of those files, and you will be able to easily recognize which of them are blocked. Specialists at 411-spyware.com have noticed that this ransomware infection will block pictures, videos, music, documents, and other files. It will touch files with such extensions as .jpeg, .jpg, .lay6, .lay, .DOT, .docx, .CSV, .uot, .asf, .avi, .vmdk, .tbk, .mid, .wma, .mov, .avi, .asf, .mpeg, .dbf, .pptx, .pot, .pps, .sti, .xml, and a bunch of others. Luckily, it is not going to encrypt files that contain any of the following strings in their filenames and/or pathnames: Program Files (x86), Program Files, Temp, Thumbs.db, $Recycle.Bin, System Volume Information, Boot, Windows, and Winnt. Unfortunately, it is a really hard task to decrypt those encrypted files because their shadow copies are deleted. In order to do that, Locky Ransomware will execute this command: vssadmin.exe Delete Shadows /All /Quiet.
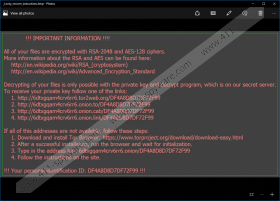
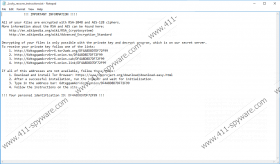
Users who infect their systems with ransomware also notice new files on their Desktop and other locations, e.g. _Locky_recover_instructions.txt and _Locky_recover_instructions.bmp. On top of that, users notice that a new Wallpaper (%UserpProfile%\Desktop\_Locky_recover_instructions.bmp) has been set without permission. This wallpaper contains the same text as files that appear on the Desktop and other directories together with the encrypted files:
!!! IMPORTANT INFORMATION !!!!
All of your files are encrypted with RSA-2048 and AES-128 ciphers.
More information about the RSA and AES can be found here:
http://en.wikipedia.org/wiki/RSA_(cryptosystem)
http://en.wikipedia.org/wiki/Advanced_Encryption_Standard
Decrypting of your files is only possible with the private key and decrypt program, which is on our secret server.
To receive your private key follow one of the links:
1. http://6dtxgqam4crv6rr6.tor2web.org/{unique ID}
2. http://6dtxgqam4crv6rr6.onion.to/{unique ID}
3. http://6dtxgqam4crv6rr6.onion.cab/{unique ID}
If all of this addresses are not available, follow these steps:
1. Download and install Tor Browser: https://www.torproject.org/download/download-easy.html
2. After a successful installation, run the browser and wait for initialization.
3. Type in the address bar: 6dtxgqam4crv6rr6.onion/{unique ID}
4. Follow the instructions on the site.
!!! Your personal identification ID: {unique ID}
As can be seen, this message provides links leading to Wikipedia in order to provide more information about the encryption it uses. In addition, it asks users to copy and paste one of the provided links into the address bar. If they do that, they end up on a page which specifically explains what needs to be done in order to download special software called Locky Decrypter. Our specialists have found that users have to a) register the Bitcoin wallet, b) purchase Bitcoins, c) transfer 0.5 BTC, and d) download the decryptor. At the time of writing, there is no other way to decrypt files; however, you should still decide responsibly whether or not to make a payment. Unfortunately, we cannot confirm that you will be able to access your files after doing that. If you do not want to risk losing money for nothing, you should recover your files from a backup, e.g. a USB flash drive. Remember, you have to delete Locky Ransomware from your system first!
In a more technical sense, Locky Ransomware will apply changes as well. It has been observed that it will also create several registry keys. Each of them have a particular function, for instance, HKCU\Software\Locky\id is responsible for the ID that is given to victims, whereas HKCU\Software\Locky\pubkey stores the RSA public key. In case of HKCU\Software\Locky\paytext and HKCU\Software\Locky\completed, which will be created too, they have particular functions as well. For example, HKCU\Software\Locky\paytext contains the text that is shown in ransom notes while HKCU\Software\Locky\completed stores information regarding the activities of ransomware, e.g. whether or not it has finished encrypting files. In fact, there is a bunch of ransomware infections that apply many changes to the system registry. Therefore, it would be really clever to take care of the system’s safety. You will definitely protect your system from harm if you install a reputable security tool on the system, update it periodically, and keep it active.
It will not be very easy to remove Locky Ransomware from the system, especially when it does not have an uninstall in Control Panel. We know that many users do not even know where to start, so we have prepared the manual removal instructions. You will find them below the article. In case you do not want to remove this threat in a manual way, you can scan your system with an automatic malware remover, such as SpyHunter. The best thing about those automatic tools is that they delete other existing infections from the system together with the main threat as well.
Delete Locky Ransomware
- Tap the Windows key + E simultaneously.
- Enter %Temp% in the address bar.
- Locate the svchost.exe file and delete it.
- Remove _Locky_recover_instructions.bmp and _Locky_recover_instructions.txt from your Desktop.
- Launch RUN (Windows key + R) and enter regedit. Click OK.
- Move to HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Wallpapers.
- Locate the BackgroundHistoryPath0 Value with the C:\Users\{user name}\Desktop\_Locky_recover_instructions.bmp Value Data. Right-click on it and select Delete.
- Move to HKCU\Control Panel\Desktop.
- Locate the Wallpaper value and delete its Value Data. Click OK.
- Remove the following registry keys one after the other:
- HKCU\Software\Locky
- HKCU\Software\Locky\id
- HKCU\Software\Locky\pubkey
- HKCU\Software\Locky\paytext
- HKCU\Software\Locky\completed 1
You should empty the Recycle Bin and reboot your computer as well after you finish erasing Locky Ransomware.
Locky Ransomware Screenshots: