Mosk Ransomware Removal Guide
Mosk Ransomware encrypts photos, documents, and all other personal files that exist on your Windows operating system. Unfortunately, once files are encrypted, it is possible that they will be undecryptable. Our malware researchers point out that this malware belongs to the STOP Ransomware family, and a tool called ‘STOP Decryptor’ has been released by malware analysts. Sadly, when we analyzed the threat, it was not yet decryptable by the tool. Hopefully, things will change in the future. All in all, even if you cannot restore your personal files right away, you do not want to pay attention to the demands that are introduced to you by the attackers behind the infection. They built the threat to make a pretty penny, and if they successfully invade your operating system, they will do everything and anything to trick you out of your savings. Hopefully, you do not need to worry about this, and you can focus on deleting Mosk Ransomware.
Just like Rote Ransomware, Msop Ransomware, Zobm Ransomware, and other clones, the malicious Mosk Ransomware spreads with the help of misleading spam emails containing malicious attachments. It also be can spread by exploiting remote access vulnerabilities and bundled downloaders. If you do not have security software that could detect and remove Mosk Ransomware right away, the infection is likely to slither into your operating system silently and then encrypt all personal files. After this, you should find the “.mosk” extension attached to the files’ names, and even though this extension is removable, your files will not be restored if you waste your time on that. The truth is that your files were encrypted using a complex encryptor, and it cannot be deciphered that easily. As we mentioned earlier, even a legitimate file decryptor is not always apt to decipher it in time. Of course, this is exactly what the attackers want because if you cannot recover files yourself, you might choose to follow their instructions.
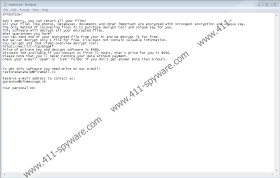
The instructions created by Mosk Ransomware creators are introduced via “_readme.txt,” a ransom note file that is likely to have multiple copies in all affected folders. The note starts with this statement: “ATTENTION! Don't worry, you can return all your files!” Without a doubt, this creates hope that some victims might be desperate for, and they might cling to it too hard. These victims might believe the promises made by cybercriminals, and that might be the worst decision. According to our experts, if you email the attackers at restoredatahelp@firemail.cc and gorentos@bitmessage.ch to receive information about the ransom payment and then pay it, the only thing that will change will be the amount of money you have. No decryptor will be presented to you in return, and that is why we DO NOT advise paying the ransom. The only thing we advise doing is removing Mosk Ransomware. Your files will not be restored in the process, but we hope that you will be able to employ a decryptor or replace the encrypted files with backups.
To put it simply, you are unlikely to obtain a decryptor even if you immediately email the attackers and pay the ransom in full as instructed. Mosk Ransomware is a real threat, but the promises made by the cybercriminals behind it are unlikely to be real. Of course, this is not something you need to worry about if you can employ a free decryptor or use backups to replace the encrypted files, but even if you have no way of recovering/replacing files, you do not want to fulfill cybercriminals’ demands. If you choose to take a gamble, do so at your own risk. What we can help you with is the removal of Mosk Ransomware. Not all victims will be able to delete this threat manually because it is important to find and delete the launcher file – which could be anywhere – but if you employ a trusted anti-malware tool, we are sure that the threat will be deleted automatically right away. On top of that, your Windows system’s protection will be reestablished too.
How to delete Mosk Ransomware
- If you can identify the launcher file, right-click and Delete it.
- Right-click and Delete the ransom note file, _readme.txt. Eliminate all copies.
- Tap Win+E keys to access Explorer and enter %WINDIR%\System32\Tasks\ into the field at the top.
- Right-click the ransomware task named Time Trigger Task and select Delete.
- Enter %LOCALAPPDATA% into the field at the top (%USERPROFILE%\Local Settings\Application Data\ on Windows XP).
- Right-click and Delete the folder containing a malicious .exe file (the names are random, but if you check the value data in step 9, you might be able to identify it).
- Tap Win+R keys to access Run and then enter regedit into the box to access Registry Editor.
- Move to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run.
- Right-click and Delete the value named SysHelper. Check the value data to identify a malicious file in step 6.
- Empty Recycle Bin and then immediately perform a full system scan to check if you left malware behind.
Mosk Ransomware Screenshots: