Nakw Ransomware Removal Guide
If you take Windows security for granted, you might face Nakw Ransomware or any other malicious infection designed to look for flaws and backdoors using which it could slither in unnoticed. When Nakw slithers in, it encrypts files, which means that a special algorithm is employed to change the data within the files. Normally, this is used to lock the files and make them accessible to their creators only. However, cybercriminals have found a way to encrypt files to make them inaccessible to the creators. This is done so that the attackers could demand money from their victims. If you continue reading, you will learn more about the process, and you will also learn how to delete Nakw Ransomware from your operating system. To ensure that you do not face malware in the future, we also share a few practical tips that, hopefully, will help you secure your Windows operating system.
Nakw Ransomware is a clone of Toec Ransomware, Nols Ransomware, Noos Ransomware, and hundreds of other infections that are part of the STOP Ransomware family. They were created using the same code, and it appears that many of them were created by the same attackers. They usually use bundled downloaders, spam emails, or remote access vulnerabilities to drop their malware. It is dropped silently, and because the encryption process is silent too, you are unlikely to discover and remove the threat until it is too late. In fact, Nakw Ransomware is not entirely silent. Once it is executed, it mimics a Windows update notification, and while it is on the screen, the encryption is happening. Afterward, you should find that most – if not all – personal files have the “.nakw” extension attached to their names. This extension can be removed, but there is no reason to do that because your files can be restored that way. In fact, at the time of research, there was no sure way to restore files. Although a tool called “STOP Decryptor” exists (it was created by malware experts and is free to use), it cannot decrypt all versions, and the Nakw variant was not decryptable when we checked last.
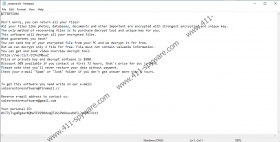
Obviously, the encryption of files is not the end goal for the creators of Nakw Ransomware. Once files are encrypted, the “_readme.txt” file is dropped, and it informs victims that they need to obtain a unique key and a decryptor to have their files restored. This is not the kind of stuff you can download online because only the creator of the encryptor has the decryptor, unless the encryption algorithm is cracked, but that does not happen too often. Of course, the creator of Nakw Ransomware suggests that they can provide you with the decryptor if you pay a ransom. It is stated that the sum is $490 within the first 72 hours and $980 afterward. To learn about the payment, you are supposed to contact the attackers at salesrestoresoftware@firemail.cc or salesrestoresoftware@gmail.com. Hopefully, you know well enough that contacting cybercriminals is a terrible idea and that paying the ransom does not guarantee anything. More likely than not, you would be left empty-handed if you pay the ransom.
We have a manual Nakw Ransomware removal guide ready for you, but we cannot guarantee that you will be able to follow it successfully. The first step suggests deleting all recently downloaded files, and that is the best option you have if you cannot identify the launcher file. If you know exactly where it is, this will not be a problem for you, but if you cannot find it or eliminate it by deleting recently downloaded files, you will not succeed. What then? Install an automated anti-malware program. This program will have no trouble removing Nakw Ransomware components, and you will also be able to forget about Windows security, because that too will be taken care of. To ensure full protection, always keep security software up-to-date, and avoid opening spam emails or downloading strange files. Also, do not forget to install updates and backup files, because if backups exist – replacements exist.
N.B. If you want to continue discussing the threat, you should add questions to the comments form below.
How to delete Nakw Ransomware
- Delete suspicious files you might have downloaded recently.
- Simultaneously tap Win+E keys on the keyboard to access Windows Explorer.
- Type %HOMEDRIVE% into the field at the top and tap Enter.
- Delete the file named _readme.txt and the folder named SystemID.
- Type %LOCALAPPDATA% into the field at the top and tap Enter.
- Delete the folder that was created by the ransomware. The name is random.
- Exit Windows Explorer and then Empty Recycle Bin.
- Install a malware scanner you trust and perform a full system scan.
Nakw Ransomware Screenshots: