Nbes Ransomware Removal Guide
Do you suspect that Nbes Ransomware has invaded your operating system? You do not need to speculate. Just look at your personal files, and if you can find the “.nbes” extension appended to their names, you can be sure that this is the infection you are dealing with. It is not the worst kind of file-encryptor out there, but it could, potentially, destroy your personal files. There are some file-encryptors that encrypt system files or wipe data altogether. Nbes is not that. Most infections of this kind are undecryptable, and it is possible that victims of Nbes could have their files restored for free. That is because this infection comes from the STOP Ransomware family – just like Hets Ransomware, Kodc Ransomware, Mosk Ransomware, and many others – and STOP Decryptor was created. Will it decrypt your personal files? We cannot know for sure, but that certainly beats paying the ransom. Can you recover the files by deleting Nbes Ransomware? You cannot, but this infection must be removed, and we discuss the methods that you can employ to achieve this.
It might be hard for you to pinpoint the moment Nbes Ransomware slithered into your operating system because that is meant to be a silent action. However, if you can link the infection to a new file you recently downloader or a spam email attachment you recently opened, perhaps you can find and remove the launcher of this malicious threat. Even though that will not save your files, it will ensure that this malware can no longer affect your personal security. This is especially important if you are going to replace the corrupted files with backups. All Windows users should have backups of their personal files stored someplace safe (e.g., a virtual cloud), and if you are prepared, Nbes Ransomware and its clones will not threaten you too much. As soon as you remove this malware, you can replace the corrupted files with copies. Unfortunately, not all users take care of their personal files in such a manner, in which case, the free decryptor is the only option left. What if it does not work for you or if it does not decrypt all of your files? In this case, you might contemplate the demands of cybercriminals.
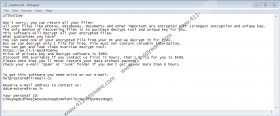
Just like most STOP Ransomware infections, Nbes Ransomware uses a file named “_readme.txt” to deliver information, demands, and instructions. The message is usually the same in every case, and the only detail that changes is the email address. Sometimes, even email addresses remain the same, which indicates that the same attackers stand behind different infections. From what we have seen, it looks like Nbes Ransomware uses unique email addresses (helprestore@firemail.cc and datarestore@iran.ir), but they are very similar to those linked to other threats, which is why it is possible that someone is trying to cover the tracks. Just like in all other cases, the ransom note message instructs to send one encrypted file to the attackers via email to receive instructions on how to pay the ransom of $490. The attackers are meant to decrypt one file for free to prove that decryption is possible, but that proves nothing. If you pay the requested ransom, you are unlikely to receive a decryptor, and so besides losing files, you would also lose your money. Hopefully, you can use a free decryptor or replace files using backups.
Are you ready to remove Nbes Ransomware from your operating system? Hopefully, you are, and all you need to do is choose the right method. Since the location and name of the .exe file that launched the infection are unknown, we advise using anti-malware software because it can delete Nbes Ransomware automatically. Even if you are able to find and delete all malware components manually, we advise implementing this software because you need reliable protection. If your Windows operating system remains unguarded, it could become the target of another ransomware infection or, perhaps, a different kind of threat, such as a malware-downloading Trojan, a password-stealing keylogger, or a CPU-exploiting miner. So, install trusted anti-malware software, create backups of all important personal files, and do not forget to stay away from spam emails, malicious downloaders, and other backdoors that crooks could exploit.
How to delete Nbes Ransomware
- Right-click and Delete the launcher of the ransomware.
- Launch Windows Explorer (tap Win+E keys).
- Enter %HOMEDRIVE% into the bar at the very top.
- Right-click and Delete a file named _readme.txt.
- Right-click and Delete a folder named SystemID.
- Enter %LOCALAPPDATA% into the bar at the very top.
- Right-click and Delete a malware folder with a random name.
- Empty Recycle Bin to complete the removal.
- Install and run a legitimate malware scanner to check for malware leftovers.
Nbes Ransomware Screenshots: