Npsk Ransomware Removal Guide
Npsk Ransomware might have invaded your operating system silently, but you might be able to track down the moment that happened. For example, you might remember opening a spam email attachment or installing new software. The threat is meant to conceal itself so that you would not notice and remove it right away. The launcher of the infection is its most functional file, and if you do not get rid of it right away, it performs the entire attack within moments. It scans the system to find specific files – such as photos and documents – and then encrypts them. Once the data of the files is ciphered, their owners cannot read them, which basically means that the files are locked. Deleting Npsk Ransomware is very important, but your files will not be restored if you do it. Hopefully, there is a way for you to recover your files, but if that is not possible, make sure you learn from your mistakes and do not repeat them again.
As our researchers point out, Npsk Ransomware was built using the STOP Ransomware code, just like Opqz Ransomware, Lezp Ransomware, Mpaj Ransomware, and hundreds of other variants. According to our malware researchers, these variants are practically identical, and there is little doubt that they were created by the same attackers. Once inside the operating system, Npsk Ransomware silently encrypts all files that are considered to be personal. This is done on purpose because the attackers want to make sure that you are invested. If you are invested in getting your personal files back, it should be easier to manipulate you into taking certain actions. To make sure that you understand what is expected from you, the attackers drop a file named “_readme.txt.” This is the file that is dropped by all STOP Ransomware variants, and the message is always the same as well. Sometimes, new email addresses are introduced, but they are combined in ways that lets us know that the same attackers stand behind them.
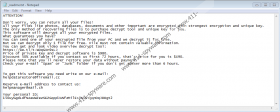
The main message of the Npsk Ransomware ransom note is that you can recover the corrupted files. The files with the “.npsk” extension attached to them are the ones that the infection, allegedly, can restore, but only if you do certain things. First, you are supposed to send a message to cybercriminals either at helpdatarestore@firemail.cc or helpmanager@mail.ch. What would happen if you did this? First, you would get instructions on how to pay the ransom in return for an alleged decryptor. That is the entire scam. Later on, however, your inbox could be flooded with misleading and intimidating messages, and that is why you do not want to contact cybercriminals. You also do not want to waste $490 on a Npsk Ransomware decryptor that allegedly can restore files. That is because even if a tool like that exists, the attackers will not give it to you. They simply do not need to. Luckily, a free tool called ‘STOP Decryptor’ was created, and you might be able to restore some or even all files. Unfortunately, that is not a given, and the only thing that can guarantee complete restoration of files is backup copies that you might have stored online or on external drives.
We cannot promise you that you will be able to restore or replace the corrupted files after removing Npsk Ransomware. We also cannot promise that you will be able to remove this infection manually using the guide below. On the other hand, if you choose to install a trusted anti-malware tool, we can promise you that you will have the infection deleted fully and completely. Moreover, you will have your entire operating system protected, which is very important as well. If you cannot replace the corrupted files afterward because you do not have copies, give the free decryptor a try, and also do not forget to figure out how to back up personal files to keep them safe in the future. Also, do not forget that cybercriminals are smart and that they can use clever spam emails and misguiding downloaders to spread malicious threats.
How to delete Npsk Ransomware
- If you know where the launcher of the infection is, find it.
- Right-click the malicious file and choose Delete.
- Tap Win and E keys at the same time to access File Explorer.
- Enter %LOCALAPPDATA% into the quick access field.
- Right-click and Delete the folder that belongs to the threat.
- Enter %HOMEDRIVE% into the quick access field.
- Right-click the file named _readme.txt and choose Delete.
- Right-click the folder named SystemID and choose Delete.
- Install a trusted malware scanner.
- Scan your system for leftovers and remove if any are found.
Npsk Ransomware Screenshots: