ProLock Ransomware Removal Guide
ProLock Ransomware is a malicious application that appends the .proLock extension to its targeted files. Unfortunately, once the malware is done, victims’ files not only look different but also become unreadable. That is because the threat uses a secure encryption algorithm to encipher each targeted file. The process can be reversed only with special decryption tools that the malicious application’s developers claim to have. They promise to send such tools to victims who pay the ransom, but, of course, there are no guarantees that they will do it. Therefore, if you end up receiving this malware, we advise thinking carefully before you decide what to do. First, you may want to learn more about the threat, and you can do so if you read the rest of this article. Also, do not forget to check the deletion instructions located below that show how to remove ProLock Ransomware manually.
Receiving threats like ProLock Ransomware can be very unpleasant and troublesome if you do not back up your files regularly. Fortunately, if you know how such malicious applications are spread, you might be able to protect your system against them. Our specialists say that most of them travel either via questionable websites or malicious emails. Thus, stopping yourself from opening files that come from unreliable sources is one of the ways to stay away from threats like ransomware. If you want to open a file, but you are not entirely sure that it is safe to launch it, we recommend scanning it with a trustworthy antimalware tool first. Also, a lot of similar malicious applications are spread through unsecured RDP (Remote Desktop Protocol) connections, which is why you should secure such connections and disable them when you do not use them.
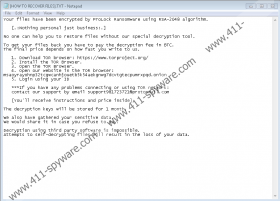
If ProLock Ransomware slips in, the malware should place some files on the %ALLUSERSPROFILE% directory. The malicious application might make them look like pictures and documents so that they would not seem suspicious. After the threat creates the described files, it should start encrypting files available on the infected computer. Our specialists say that it ought to encipher all files except data with the following extensions: .bac, .bak, .bat, .bkf, .chm, .cmd, .dll, .dsk, .hlf, .ico, .inf, .ini, .lng, .lnk, .msi, .set, .sys, .ttf, .vhd, .wbc, .win, .exe. Just as we said earlier, each encrypted file ought to receive the .proLock extension, for example, panda.jpg.proLock. The minute all the targeted files get encrypted, ProLock Ransomware should create a ransom note called [HOW TO RECOVER FILES].TXT in every affected directory.
The malware’s ransom note should say that encrypted files cannot be decrypted without tools belonging to the threat’s creators. Thus, the rest of the note is dedicated to explaining how to contact the hackers behind the malicious application and pay ransom. Dealing with cybercriminals is risky and could end up badly if they decide not to bother with sending you the promised decryption tools. Thus, we advise not to rush into it and think carefully if your data is worth the risk. No matter what you choose to do, we recommend erasing ProLock Ransomware. If you want to get rid of the ransomware manually, you could use the deletion instructions placed below. Of course, if the task looks too difficult, you could get a reliable security tool that would safely remove ProLock Ransomware from your system.
Get rid of ProLock Ransomware
- Click Ctrl+Alt+Delete.
- Pick Task Manager and go to the Processes tab.
- Check if there is a process belonging to the ransomware.
- Select it and press the End Task button.
- Close Task Manager.
- Press Win+E.
- Go to the paths:
%USERPROFILE%\Desktop
%USERPROFILE%\Downloads
%TEMP% - Look for a recently obtained file that might have infected your device, right-click it, and choose Delete.
- Navigate to this path: %ALLUSERSPROFILE%
- Right-click the following files separately and press Delete to erase them:
WinMgr.xml
WinMgr.bmp
clean.bat
run.bat - Then right-click files named [HOW TO RECOVER FILES].TXT and choose Delete to get rid of them.
- Close File Explorer.
- Empty Recycle Bin.
- Reboot the computer.
ProLock Ransomware Screenshots: