R44s Ransomware Removal Guide
When R44s Ransomware attacks, you are not supposed to realize it. That is why this infection uses disguises to slither into your Windows operating system. Of course, if the system is vulnerable, it becomes much easier for malware to invade. If the operating system is guarded, in theory, malware should not slip in unnoticed. We want to emphasize the words “in theory,” because it would be irresponsible to claim that anti-malware software can prevent 100% of malware attacks. The reality is that cybercriminals are smart, and sometimes, they are quicker than cybersecurity experts who are responsible for updating malware detections. That being said, if you secure your operating system, you are exponentially safer than without added security. Hopefully, you are able to fend off malware with legitimate anti-malware software, but if your system was hit by the ransomware before you got the chance to take care of it, we hope that you will not forget about that once you delete R44s Ransomware.
Do you remember opening a strange PDF file right before the attack of R44s Ransomware? If you do, this file could have concealed the launcher of the infection. Note that ransomware can also be spread using bundled downloaders, RDP vulnerabilities, or by other active infections. This is why it is so important to scan your operating system after you think you have removed R44s Ransomware completely. Of course, before you get to that, you have to go through the mess created by this malware. Once it is executed on the system, victims have only a few moments to remove this ransomware before it encrypts personal files. Once that is done, the “.r44s” extension is appended, and files become unreadable. Files are encrypted so that the attackers could demand money in return for their decryption, and since people are likely to be most willing to make sacrifices for personal files, that is what the infection corrupts. Unfortunately, once photos, videos, documents, and similar files are encrypted, you are stuck.
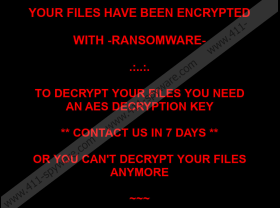
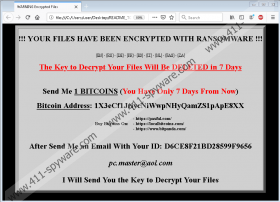
After files are encrypted, R44s Ransomware drops the “wallpaper.jpg” file to change the Desktop wallpaper. This image displays an intimidating message that instructs to contact the attackers within 7 days. The threat also drops ransom note files in 9 different languages (Chinese, Dutch, English, Farsi, French, German, Italian, Russian, and Spanish). The English version of the file is called “README_TO_DECRYPT_FILES.html,” and the message inside informs that files were encrypted and that they would be deleted in 7 days if the ransom was not paid. The ransom is 1 BTC (~$6,500) and victims are instructed to send it to the attackers’ bitcoin wallet (1X3eCf1JriycNiWwpNHyQamZS1pApE8XX). Afterward, they are supposed to send an email with a unique ID code to pc.master@aol.com. What’s the outcome of that? The attackers suggest that you would be sent a decryption key, but our researchers warn that you would be left empty-handed. So, if you do not want to waste your money for nothing, do not follow the attackers’ instructions. Also, do not contact them, unless you want your inbox to be flooded with misleading and intimidating messages.
We have prepared a manual R44s Ransomware removal guide, and we hope that you will be able to follow it for a full removal of the infection. Unfortunately, the launcher of the threat could be located in a random folder with a random name, and if you cannot find it, you might be unable to perform the removal of R44s Ransomware yourself. That is not a tragedy, because even if you can delete the infection manually, we still recommend installing legitimate anti-malware software. This software can automatically delete R44s Ransomware and any other threats that might exist on your computer without your knowledge at all. Furthermore, it can provide you with reliable Windows protection, which, as you know, can decrease your chances of facing malware in the future. After you delete R44s Ransomware, hopefully, you can replace the encrypted files with backups stored online or on external drives. If you do not own backup copies, make sure you do not forget to create copies in the future.
How to delete R44s Ransomware
- Go to the Desktop and Deletethese files:
- wallpaper.jpg
- README_TO_DECRYPT_FILES.html
- LEGGIMI_PER_DECIFRARE_I_FILES.txt
- LESEN_SIE_MICH_UM_DATEIEN_ZU_ENTSCHLUSSELN.txt
- LISEZ-MOI_POUR_DECHIFFRER_LES_FICHIERS.txt
- LEAME_PARA_DESCIFRAR_ARCHIVOS.txt
- LEESMIJ-BESTAND_VOOR_HET_DECODEREN_VAN_BESTANDEN.txt
- PROCHTI_MENYA_DLYA_RASSHIFROVKI_FAYLOV.txt
- شروع_رمزگ_شایی.txt
- 重新解密文件.txt
- Tap Win+E on keyboard to access File Explorer.
- Enter %PUBLIC% into the field at the top.
- Delete the ransom note files and a malicious {random name}.exe file.
- Enter %APPDATA% into the field at the top.
- Delete a malicious {random name}.exe file.
- Tap Win+R keys on the keyboard to launch Run.
- Enter regedit into the box and click OK to launch Registry Editor.
- Go to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
- Delete the value named Message-2019.
- Empty Recycle Bin and then quickly perform a full system scan to check for malware leftovers.
R44s Ransomware Screenshots: